GUEST ESSAY: The many ways your supply chain is exposing your company to a cyber attack
The Last Watchdog
MAY 16, 2022
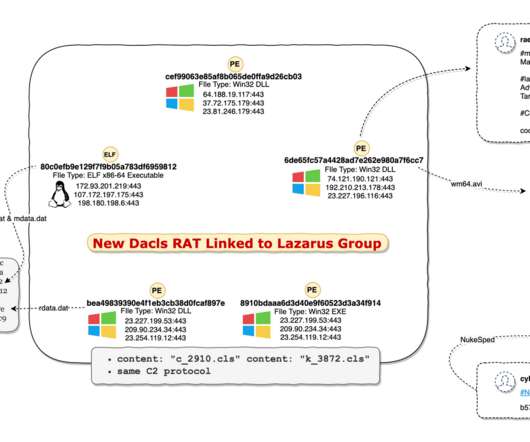
The inherent complexity of the supply chain for modern technology is a reason why so many cybercrime attempts have been successful. It provides an answer to the most common and dangerous forms of cybercrime: •Security at the root. The TCU deploys AI-based runtime threat-detection surveillance and remediation for enhanced tamper •.
































Let's personalize your content