16 Best DDOS Attack Tools in 2022
Security Boulevard
JANUARY 23, 2022
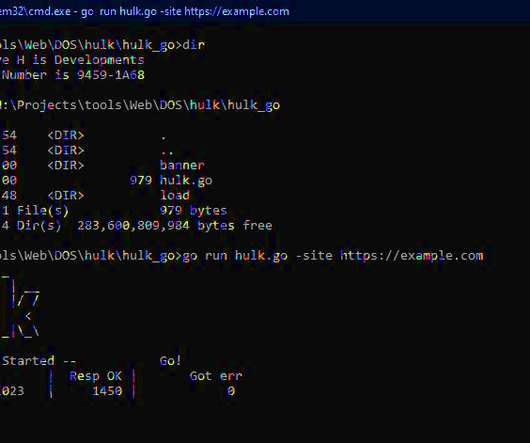
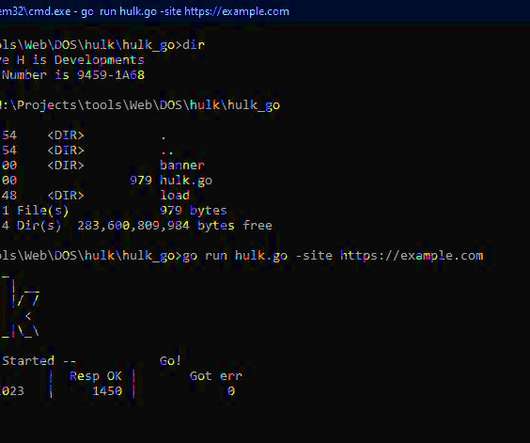
What are DDOS attack tools? DDOS attacks are cyber- attacks targeted at rendering certain computers, network systems and servers non-functional. Attackers have to carry out a long series of actions that involve social engineering, data breaches and sometimes even system testing.





















Let's personalize your content