Does That Data Make Your Company a Cyber Attack Target?
CyberSecurity Insiders
JUNE 21, 2021
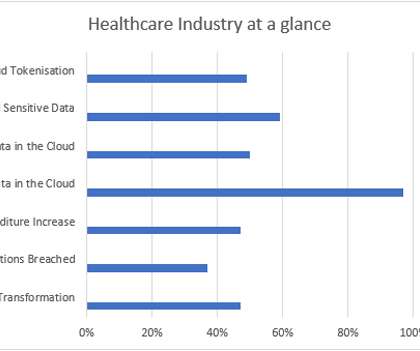
The inconvenient truth is that, while most businesses have been distracted by digital transformation (DX), sensitive data has been left on a metaphorical windowsill, like a freshly baked apple pie. There is a common misconception that data security inhibits DX – but this couldn’t be farther from the truth.


























Let's personalize your content