LockBit ransomware group claims to have hacked Bridgestone Americas
Security Affairs
MARCH 13, 2022
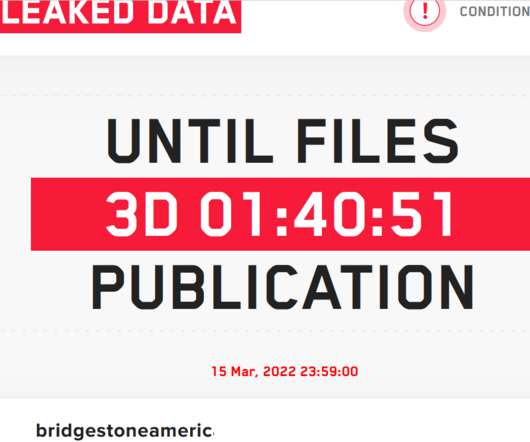
Lockbit operators plan to release the stolen data by March 15, 2022 23:59, if the company will not pay the ransom. On February 27, some company employees at Bridgestone’s La Vergne plant reported being sent home due to a possible cyber attack. We are only interested in money for our harmless and useful work.














Let's personalize your content