Black Hat insights: Getting bombarded by multiple ransomware attacks has become commonplace
The Last Watchdog
AUGUST 15, 2022
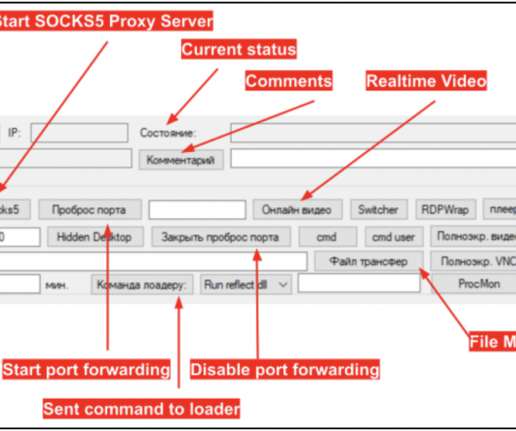
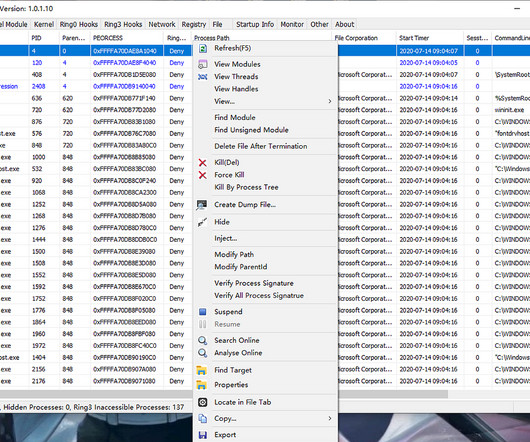
And if an enterprise is under an active ransomware attack, or a series of attacks, that’s a pretty good indication several other gangs of hacking specialists came through earlier and paved the way. In short, overlapping cyber attacks have become the norm. Configure system administrative tools more wisely.




































Let's personalize your content