How to Use Your Asset Management Software to Reduce Cyber Risks
CyberSecurity Insiders
APRIL 29, 2022
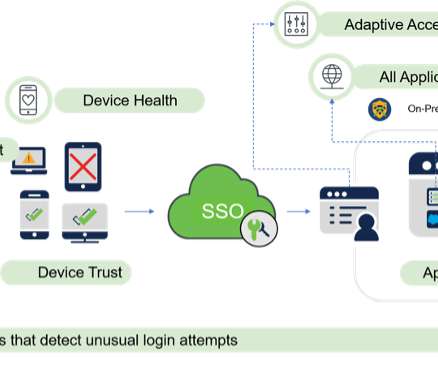
Yes, one lapse on a spam email, one inadequate password, one abandoned account, or a malfunctioning asset can cause havoc. . Here is a rundown of the benefits of an asset management software in cutting down cyber-related threats. Identify assets and their associated risks. Handle the threats’ possible risks. .


















































Let's personalize your content