Web Hacking Service ‘Araneida’ Tied to Turkish IT Firm
Krebs on Security
DECEMBER 19, 2024
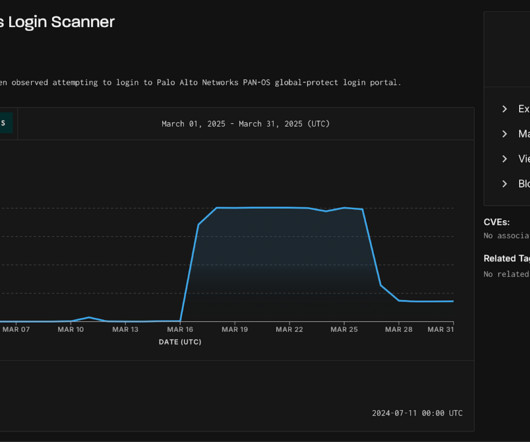
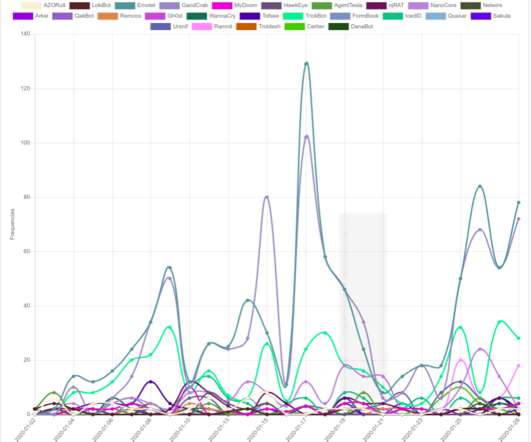
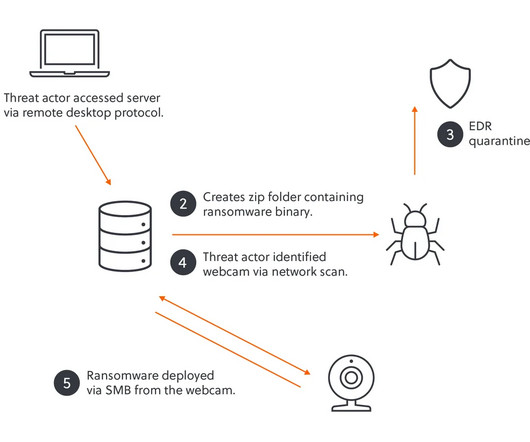
The cracked software is being resold as a cloud-based attack tool by at least two different services, one of which KrebsOnSecurity traced to an information technology firm based in Turkey. “We have been playing cat and mouse for a while with these guys,” said Matt Sciberras , chief information security officer at Invicti.







































Let's personalize your content