The March Madness Cyber Threat
Adam Levin
MARCH 17, 2022
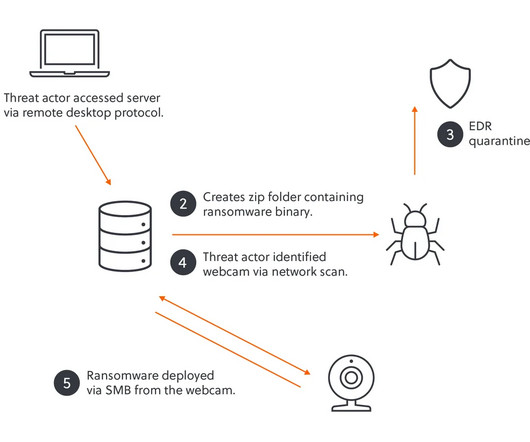
Sensitive information including passwords and financial information can be exfiltrated and ransomware can be deployed to block access to critical data. Change passwords regularly. The post The March Madness Cyber Threat appeared first on Adam Levin. Create a culture of cybersecurity and data hygiene.
















































Let's personalize your content