Cybercrime Statistics in 2019
Security Affairs
JANUARY 18, 2020
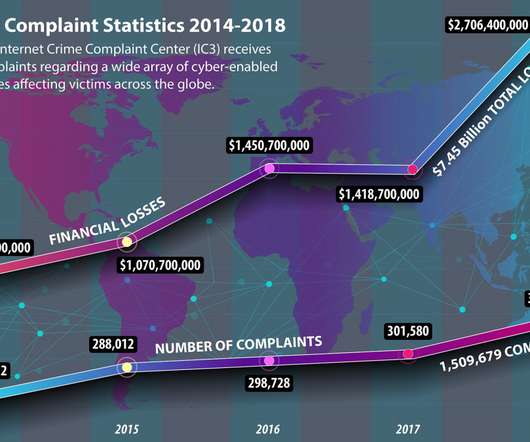
billion in 2018. billion in 2018. billion in 2018. Most financially devastating threats involved investment scams, business email compromises (BEC) , and romance fraud. The total annual cost of all types of cyberattacks is increasing. The cost of malware attacks is now an average of US$2. Source Accenture.















Let's personalize your content