Glove Stealer bypasses Chrome’s App-Bound Encryption to steal cookies
Security Affairs
NOVEMBER 15, 2024
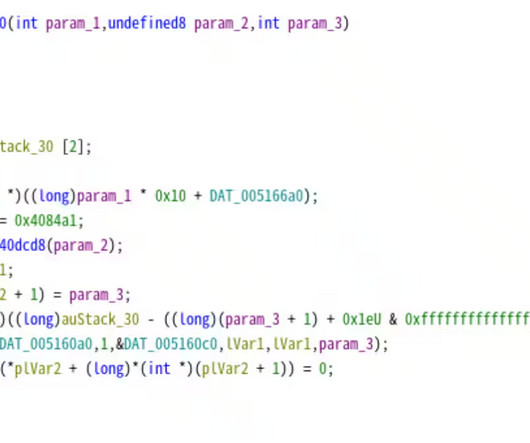
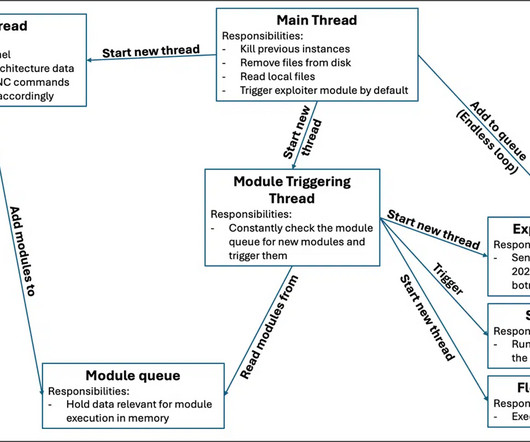
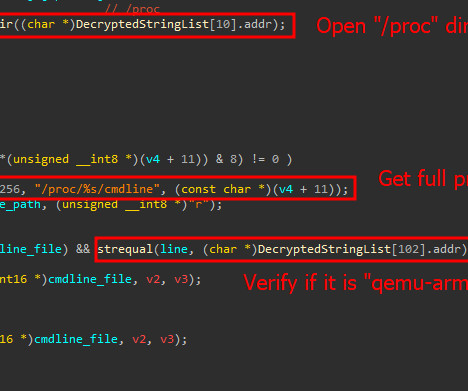
The Glove Stealer malware exploits a new technique to bypass Chrome’s App-Bound encryption and steal browser cookies. The malware bypasses Chrome’s App-Bound Encryption by utilizing the IElevator service, a method that was disclosed in October 2024. Gen Digital observed phishing campaigns distributing the Glove Stealer.







































Let's personalize your content