Cryptocurrencies and cybercrime: A critical intermingling
Security Affairs
APRIL 26, 2024
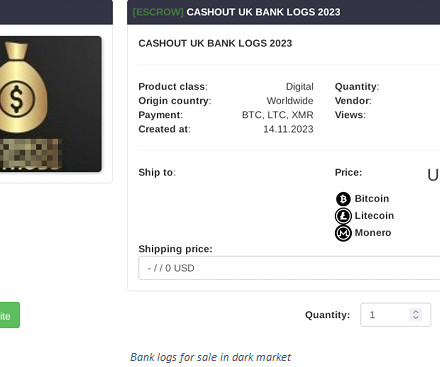
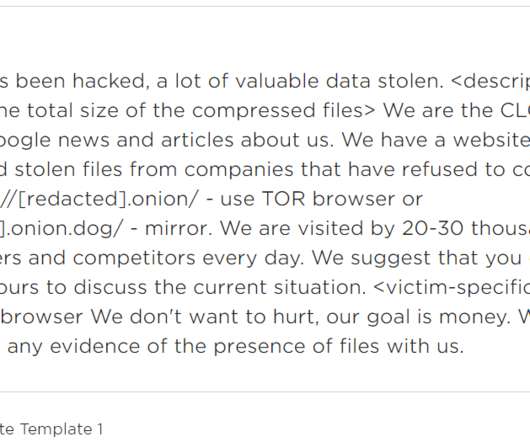
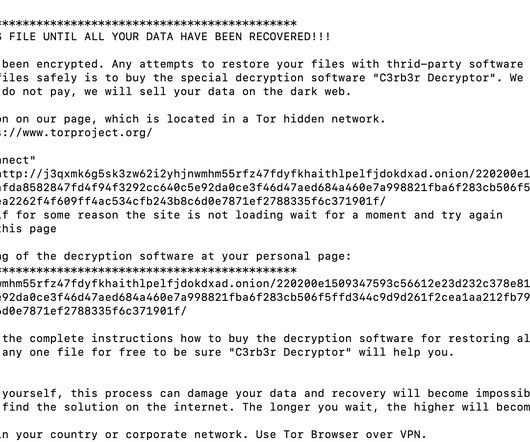
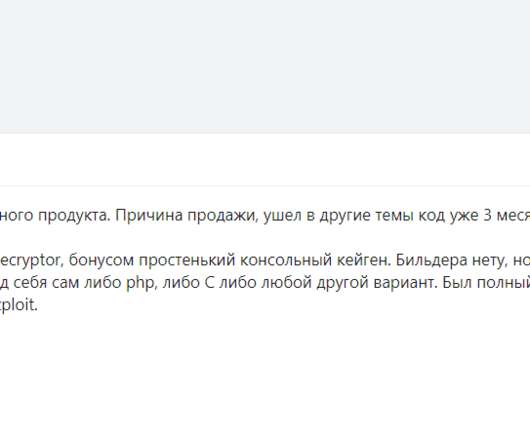
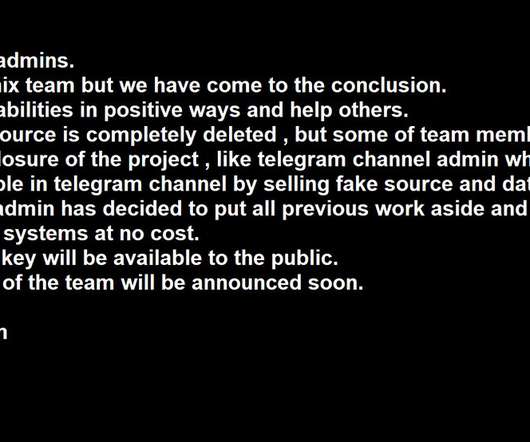
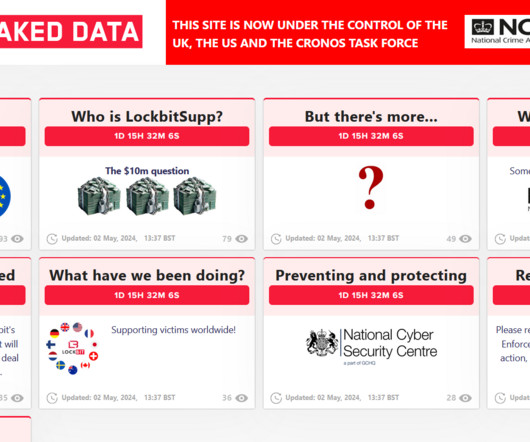
As cryptocurrencies have grown in popularity, there has also been growing concern about cybercrime involvement in this sector Cryptocurrencies have revolutionized the financial world, offering new investment opportunities and decentralized transactions.































Let's personalize your content