BunnyLoader, a new Malware-as-a-Service advertised in cybercrime forums
Security Affairs
OCTOBER 3, 2023
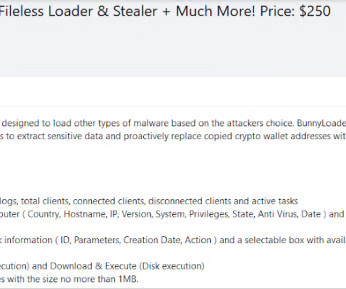
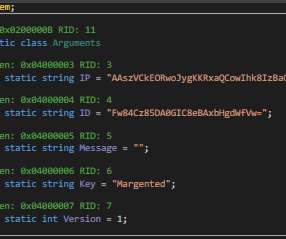
Cybersecurity researchers spotted a new malware-as-a-service (MaaS) called BunnyLoader that’s appeared in the threat landscape. Zscaler ThreatLabz researchers discovered a new malware-as-a-service (MaaS) that is called BunnyLoader, which has been advertised for sale in multiple cybercrime forums since September 4, 2023.



































Let's personalize your content