EDR-as-a-Service makes the headlines in the cybercrime landscape
Security Affairs
APRIL 7, 2025
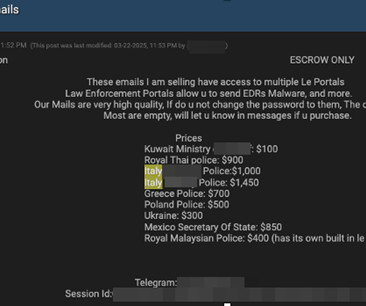
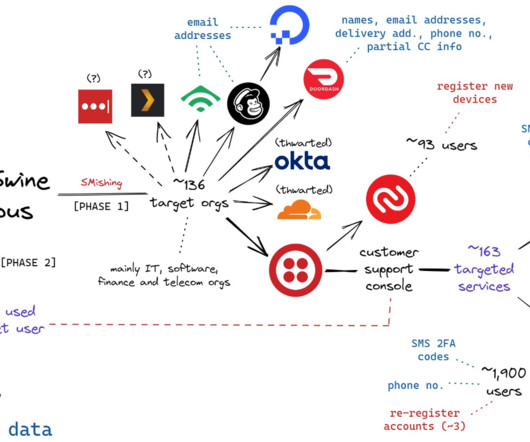
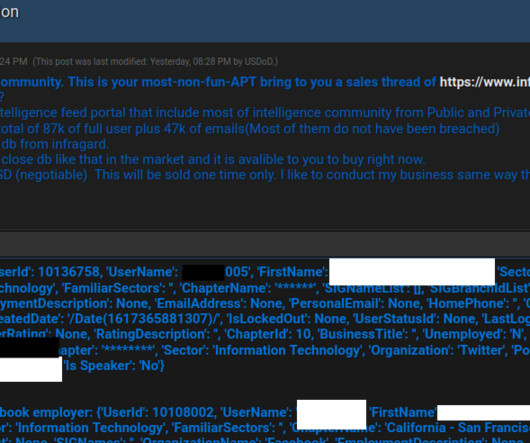
This approach reflects the as-a-service logic already prevalent in other areas of the cybercrime sector, significantly reducing the level of technical knowledge needed by those wishing to access this confidential data.
















































Let's personalize your content