The Silent Breach: How E-Waste Fuels Cybercrime
SecureWorld News
MARCH 27, 2025
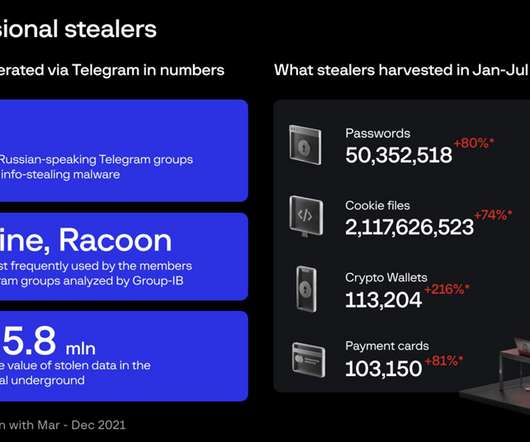
In today's digital world, cybercrime is a threat to our private data and security. And with Americans owning an average of 24 electronic items in their homes , neglecting to dispose of these items correctly is putting individuals at significant risk of cybercrime. What is cybercrime? It's time to change it.













































Let's personalize your content