Teen Hackers Behind Notorious Lapsus$ Group Convicted in London
SecureWorld News
AUGUST 28, 2023
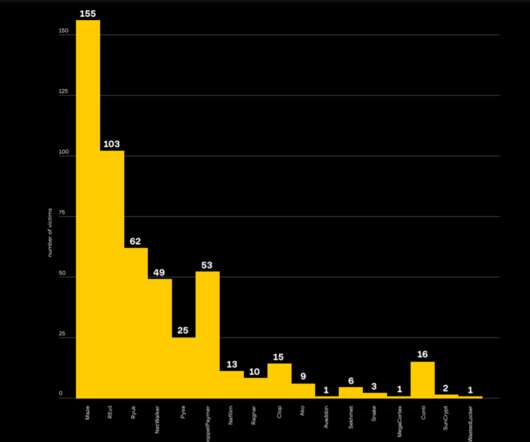
RELATED: Lapsus$ Returns One Week After 7 Teenage Hackers Arrested ] The extent of Kurtaj's involvement in cybercrimes is staggering. Their techniques included SIM swapping, prompt bombing attacks, and social engineering, which allowed them to infiltrate well-defended organizations. and another in Brazil.




















Let's personalize your content