What Is a Firewall and Do you Need One?
Adam Levin
JULY 6, 2022
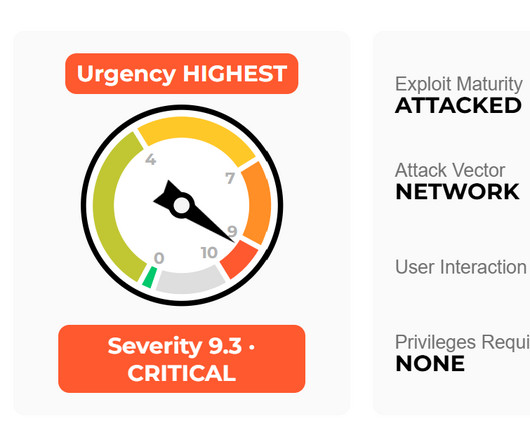
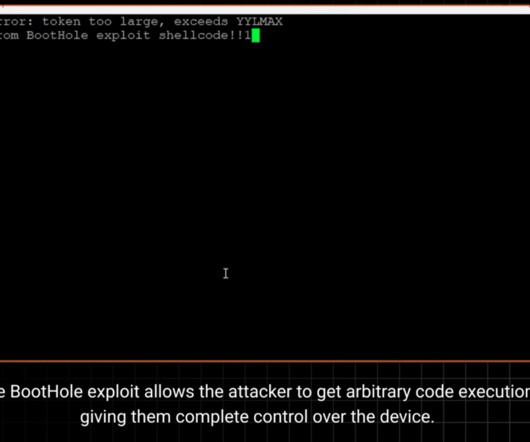
A firewall is a network security device or program designed to prevent unauthorized and malicious internet traffic from entering a private network or device. Firewalls filter incoming network traffic at a computer’s entry points, or ports, where information is exchanged between the computer network and external devices. Probably not.

















































Let's personalize your content