Five Years Later: Evolving IoT Cybersecurity Guidelines
NSTIC
MAY 13, 2025
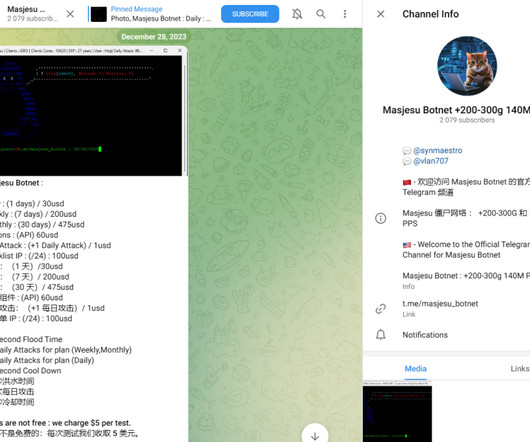
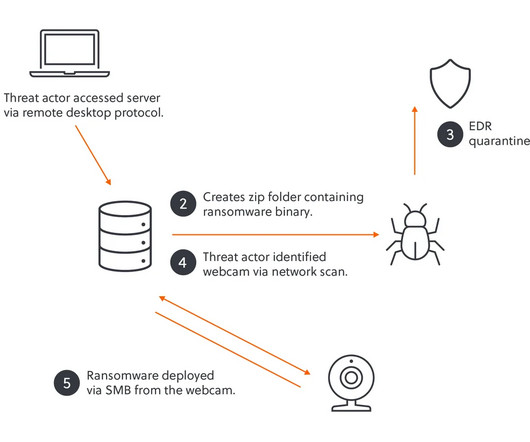
The Backgroundand NISTs Plan for Improving IoT Cybersecurity The passage of the Internet of Things (IoT) Cybersecurity Improvement Act in 2020 marked a pivotal step in enhancing the cybersecurity of IoT products.













































Let's personalize your content