Five steps to password policy compliance
IT Security Guru
JULY 23, 2021
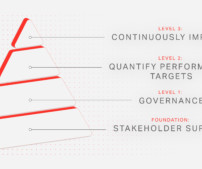
Therefore, using good password security and robust password policies is an excellent way for organizations to bolster their cybersecurity posture. What characteristics make up an effective password policy? Use account lockout policies. Contributed by cybersecurity expert Brandon Lee. Wrapping Up.

























Let's personalize your content