UnitedHealth almost doubles victim numbers from massive Change Healthcare data breach
Malwarebytes
JANUARY 27, 2025
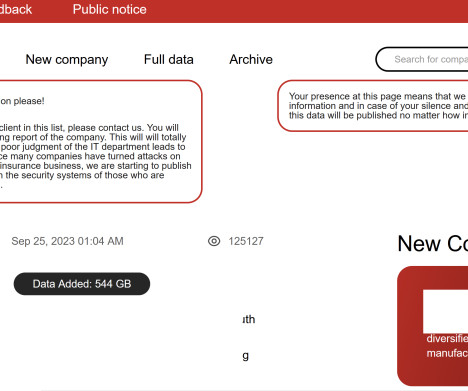
UnitedHealth says it now estimates that the data breach on its subsidiary Change Healthcare affected 190 million people, nearly doubling its previous estimate from October. The ALPHV/BlackCat ransomware group claimed the initial attack. To date, we have not yet seen full medical histories appear in the data review.














































Let's personalize your content