Introducing continuous remote worker visibility and expanded data collection with Secure Network Analytics Release 7.3.2
Cisco Security
JUNE 1, 2021
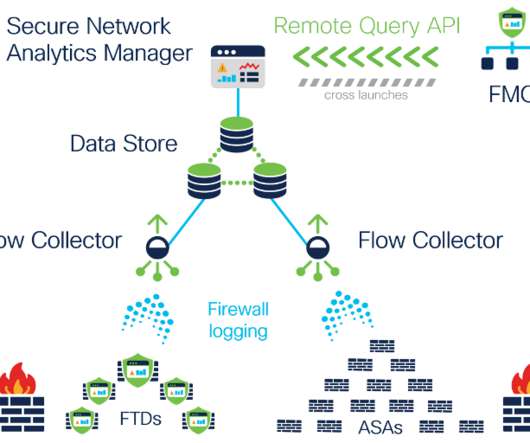
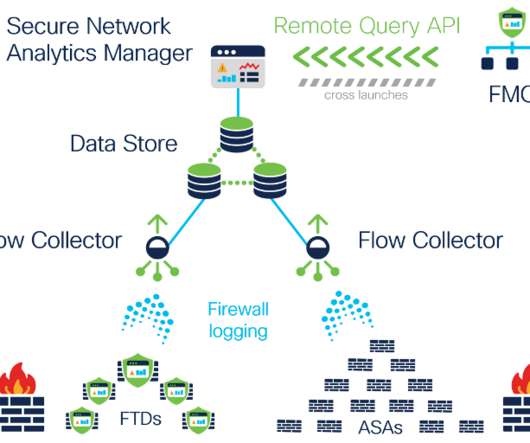
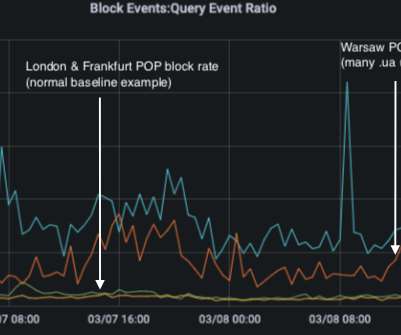
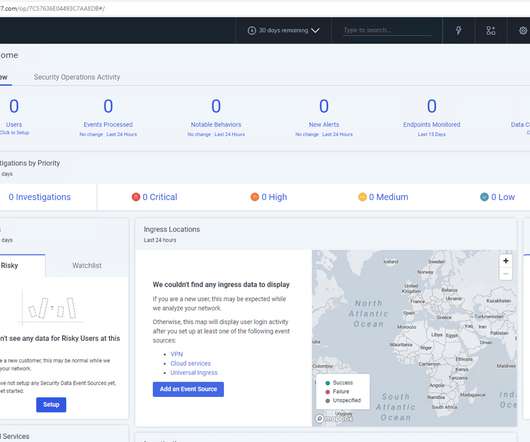
Preamble: The great network visibility blackout of 2020. Security teams can now gain visibility into activities that they were previously blind to, such as: Additionally, with Release 7.3.2, The ability to define customized security events based on NVM data-specific criteria. With release 7.3.2,

























Let's personalize your content