Top 9 Trends In Cybersecurity Careers for 2025
eSecurity Planet
OCTOBER 18, 2024
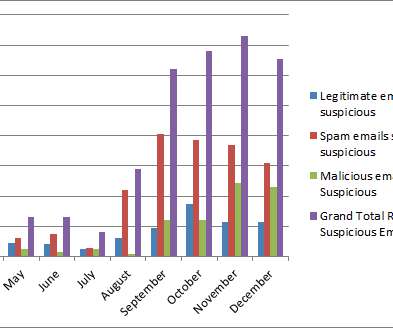
It is generalized and entry-level, but it demonstrates a core level of competency that can be a building block of almost any career in cybersecurity, whether in administration, engineering, or development. It’s obviously a step to penetration testing, but it’s also helpful for architect, engineer, and analyst jobs.
































Let's personalize your content