Enhanced Protection - The strongest level of Safe Browsing protection Google Chrome has to offer
Google Security
DECEMBER 5, 2022
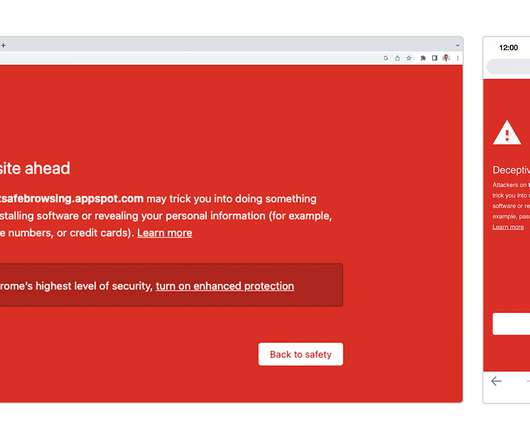
Specifically, how it came about, the protections that are offered and what it means for your data. Security and privacy have always been top of mind for Chrome. This is why Safe Browsing ’s phishing and malware protections have been a core part of Chrome since 2007.





















Let's personalize your content