Crooks target Ukraine’s IT Army with a tainted DDoS tool
Security Affairs
MARCH 10, 2022
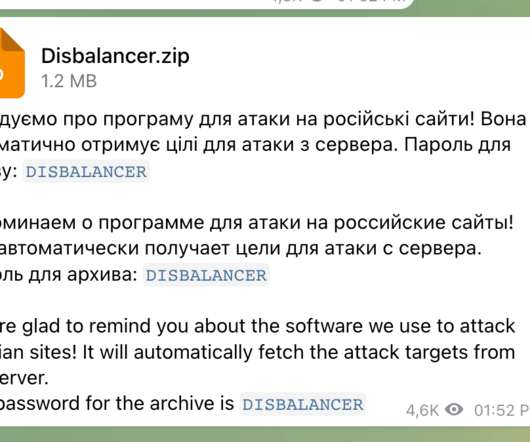
Cisco Talos researchers have uncovered a malware campaign targeting Ukraine’s IT Army , threat actors are using infostealer malware mimicking a DDoS tool called the “Liberator.” Liberator is advertised as a DDoS tool to launch attacks against “Russian propaganda websites.” Pierluigi Paganini.
















Let's personalize your content