KrebsOnSecurity Hit With Near-Record 6.3 Tbps DDoS
Krebs on Security
MAY 20, 2025
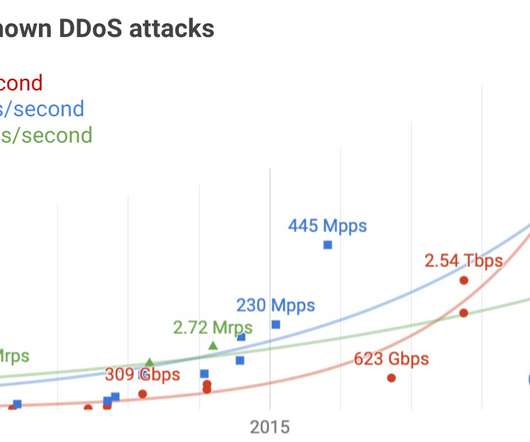
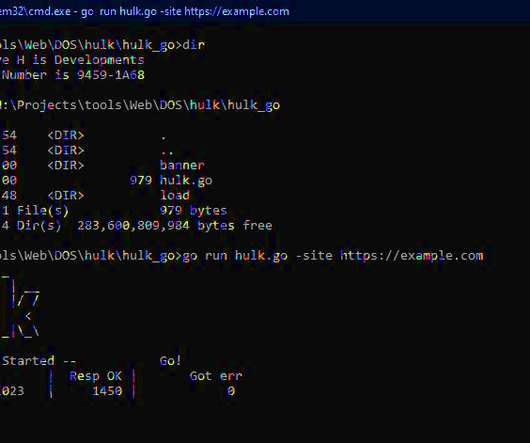
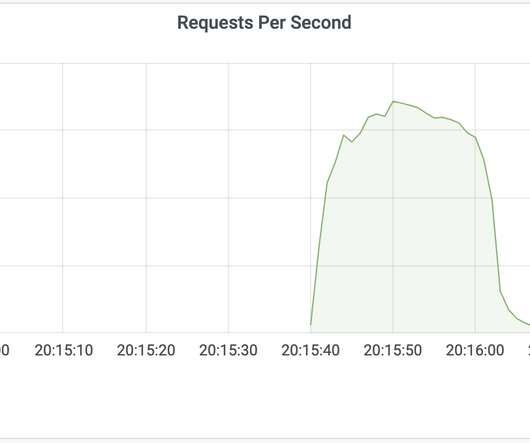
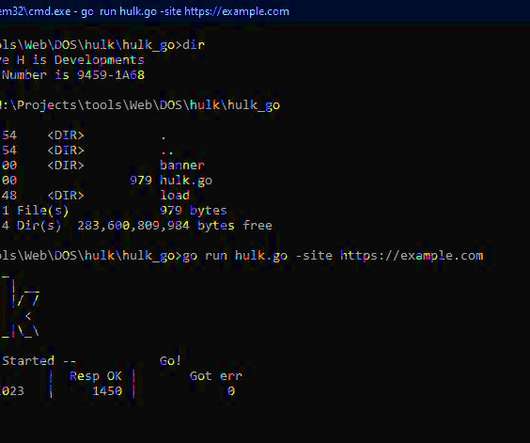
KrebsOnSecurity last week was hit by a near record distributed denial-of-service (DDoS) attack that clocked in at more than 6.3 Google Security Engineer Damian Menscher told KrebsOnSecurity the May 12 attack was the largest Google has ever handled. terabits of data per second (a terabit is one trillion bits of data).







































Let's personalize your content