BMW dealer at risk of takeover by cybercriminals
Security Affairs
DECEMBER 19, 2023
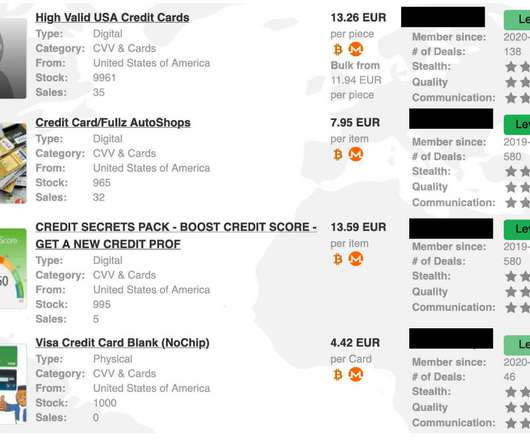
This could encompass customer information, sales records, and financial data. As a result, there’s an elevated risk of sensitive information being stolen and misused for activities such as identity theft, fraud, or sale on the dark web.















Let's personalize your content