Unraveling the truth behind the DDoS attack from electric toothbrushes
Security Affairs
FEBRUARY 8, 2024
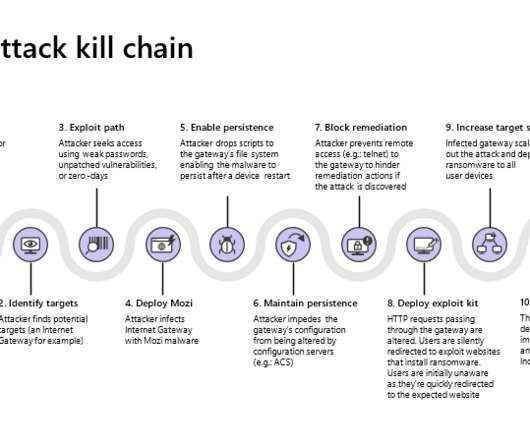
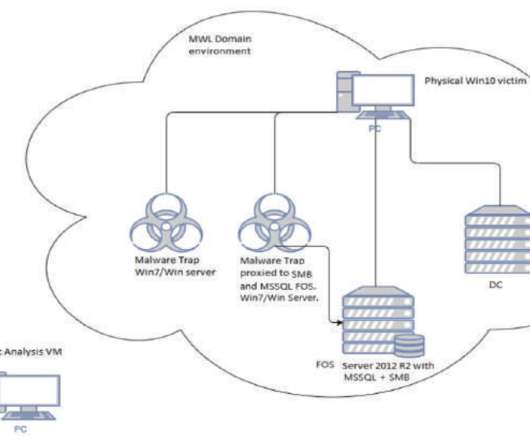
Several media reported that three million electric toothbrushes were compromised and recruited into a DDoS botnet. The Swiss newspaper Aargauer Zeitung first published the news of a DDoS attack, carried out on January 30, that involved three million compromised electric toothbrushes. Is it true? What the f is wrong with you people????















Let's personalize your content