New Charges, Sentencing in Satori IoT Botnet Conspiracy
Krebs on Security
JUNE 25, 2020
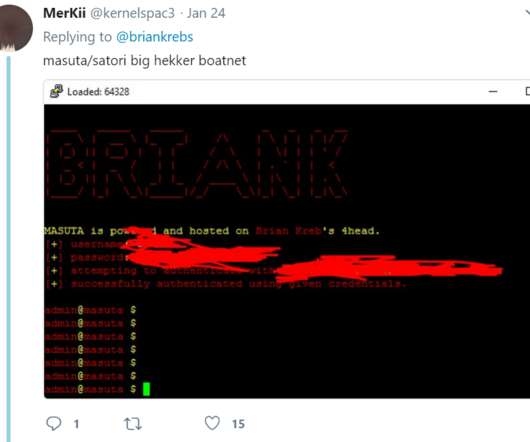
Justice Department today criminally charged a Canadian and a Northern Ireland man for allegedly conspiring to build botnets that enslaved hundreds of thousands of routers and other Internet of Things (IoT) devices for use in large-scale distributed denial-of-service (DDoS) attacks. telecommunications provider TalkTalk.













Let's personalize your content