How to Build a Security Awareness Training Program that Yields Measurable Results
The Hacker News
NOVEMBER 18, 2021
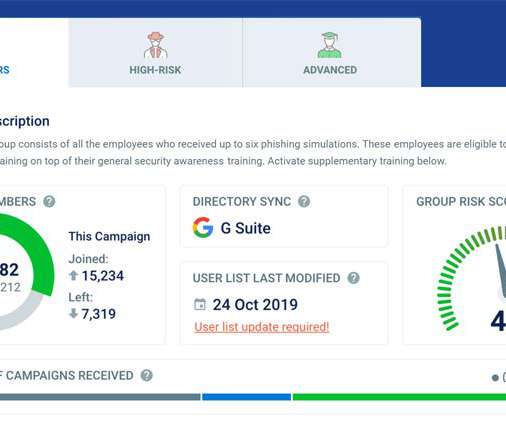
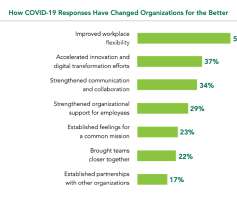
Organizations have been worrying about cyber security since the advent of the technological age. Today, digital transformation coupled with the rise of remote work has made the need for security awareness all the more critical.






























Let's personalize your content