Calling Home, Get Your Callbacks Through RBI
Security Boulevard
JANUARY 17, 2024
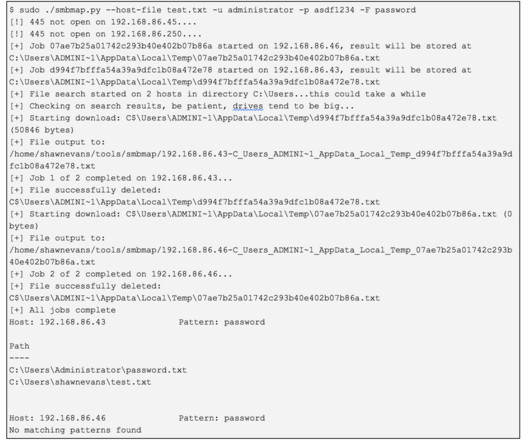
RBI solutions typically allow the configuration of file upload and download profiles, restricting the types of files that can be submitted or retrieved from websites based on multiple factors such as file extension, size, entropy/encryption of data, signatures, site reputation, and more. This can be due to encryption or even size.
























Let's personalize your content