Russia-linked Gamaredon APT targets Ukrainian authorities with new malware
Security Affairs
FEBRUARY 3, 2023
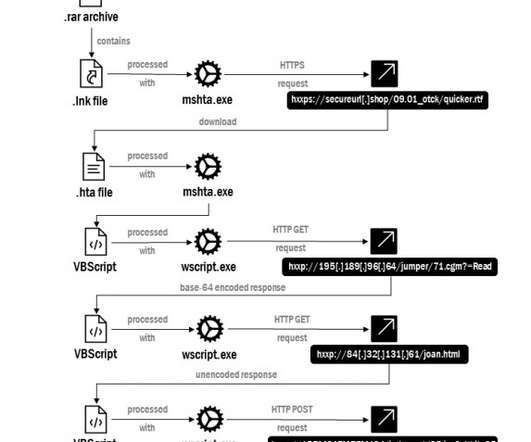
Russia-linked threat actor Gamaredon employed new spyware in cyber attacks aimed at public authorities and critical information infrastructure in Ukraine. The government experts pointed out that the threat actor continues to evolve its TTPs to avoid detection. lnk” (“Request of the Security Service of Ukraine 12-1-125 dated 09.01.2023.lnk”).


















Let's personalize your content