OneNote documents spread malware in several countries
Tech Republic Security
FEBRUARY 1, 2023
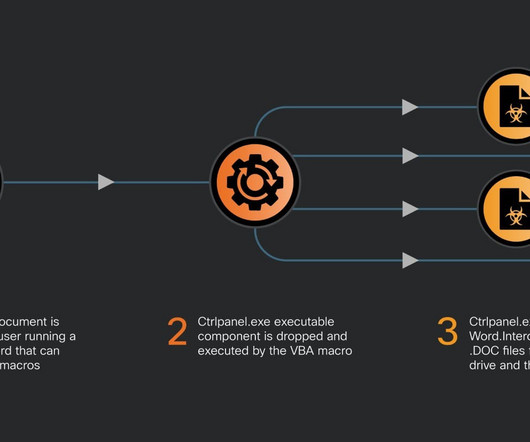
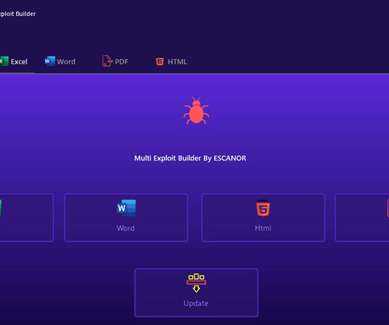
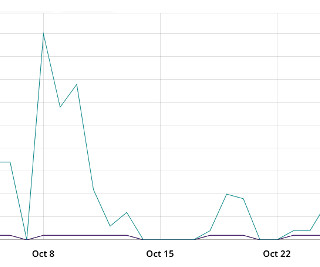
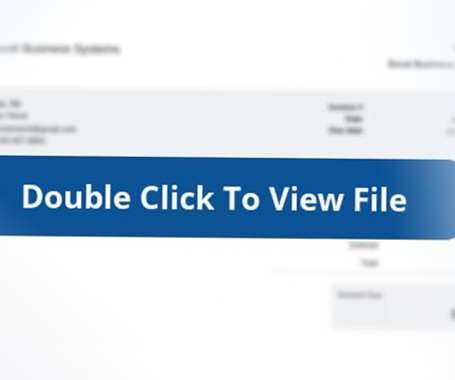
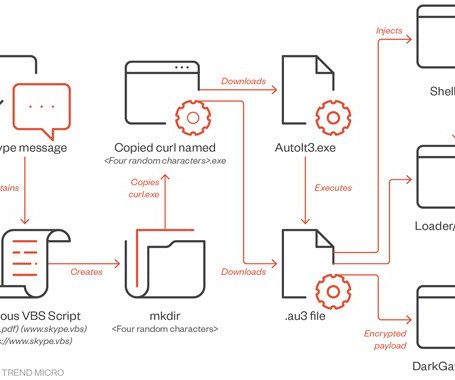
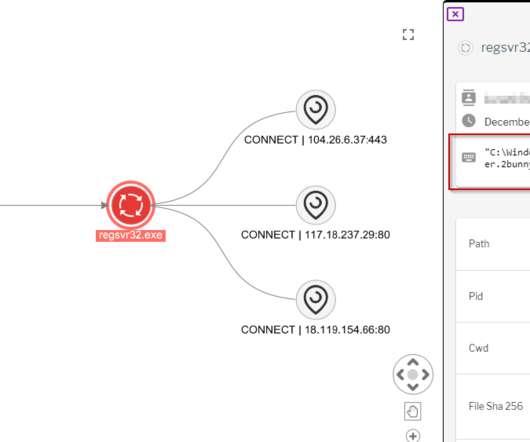
A new phishing campaign abuses OneNote documents to infect computers with the infamous AsyncRAT malware, targeting users in the U.K., The post OneNote documents spread malware in several countries appeared first on TechRepublic. Canada and the U.S.





































Let's personalize your content