Measure Security Performance, Not Policy Compliance
The Falcon's View
MARCH 12, 2018
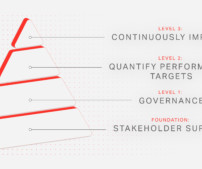
Except, of course, that in the real world nobody ever took time to read the more detailed documents, Ops and Dev teams really didn't like being told how to do their jobs, and, at the end of the day, I was frequently reminded that publishing a policy document didn't translate to implementation. Now, note a couple things here.



























Let's personalize your content