FBI: Spike in Hacked Police Emails, Fake Subpoenas
Krebs on Security
NOVEMBER 9, 2024
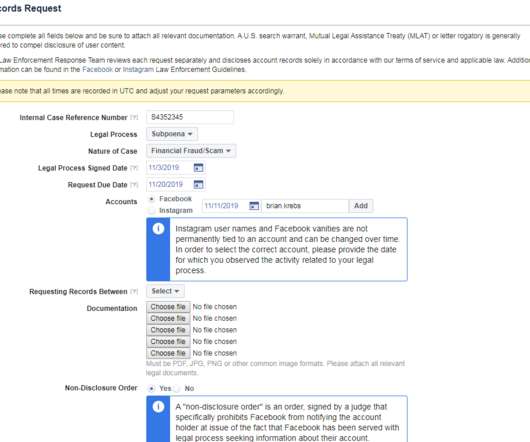
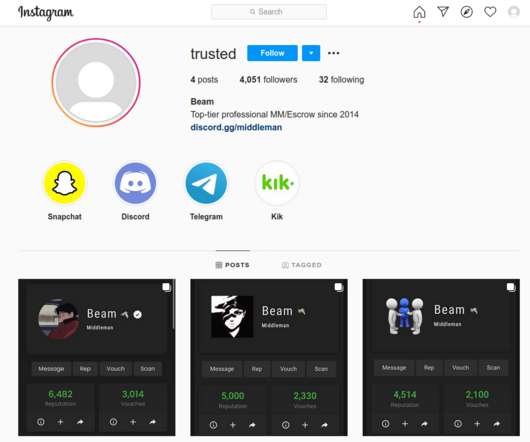
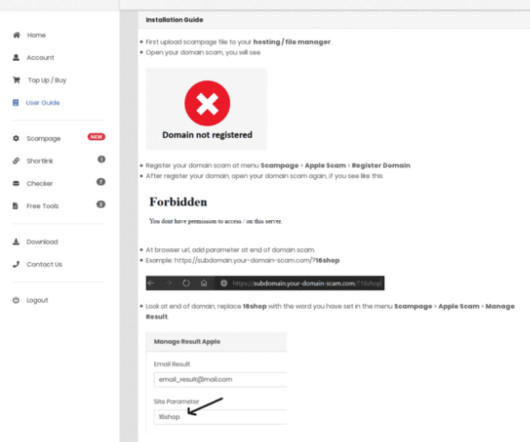
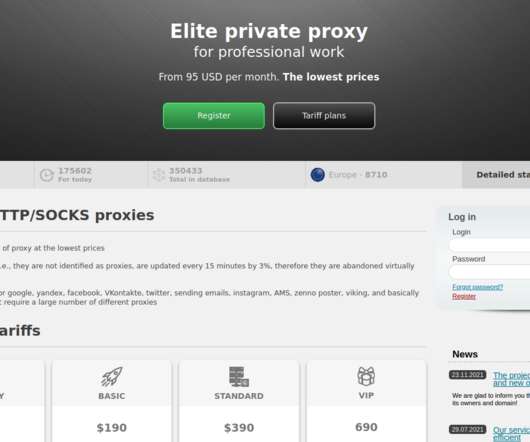
The trouble is, these EDRs largely bypass any official review and do not require the requester to supply any court-approved documents. Others simply sell access to hacked government or police email accounts, and leave it up to the buyer to forge any needed documents. “Unlimited Emergency Data Requests. . Reset as you please.







































Let's personalize your content