Using Google Search to Find Software Can Be Risky
Krebs on Security
JANUARY 25, 2024
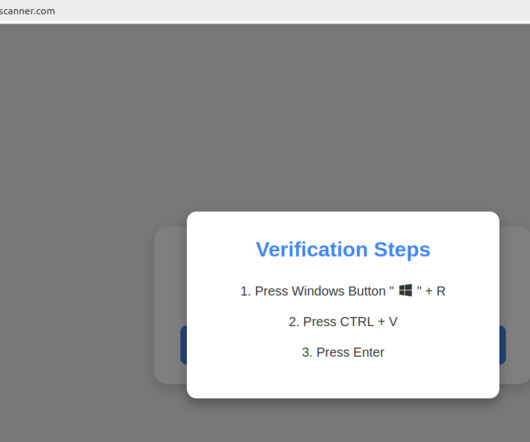
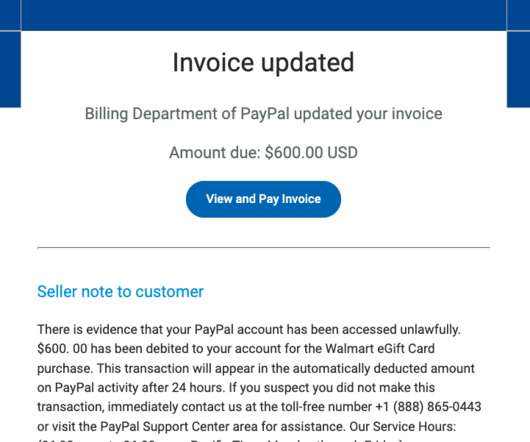
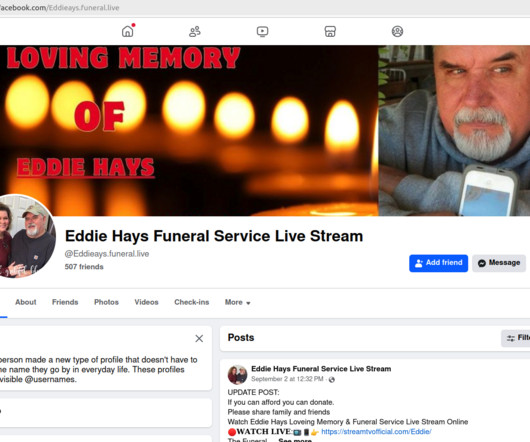
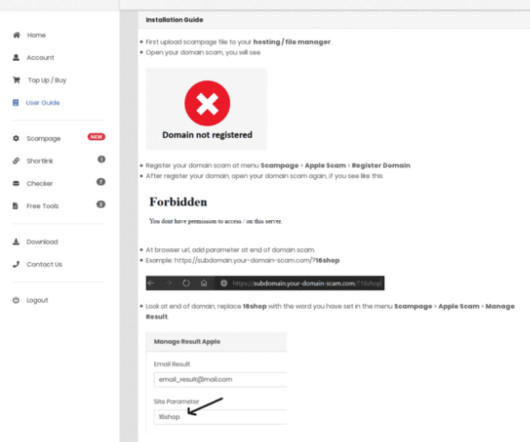
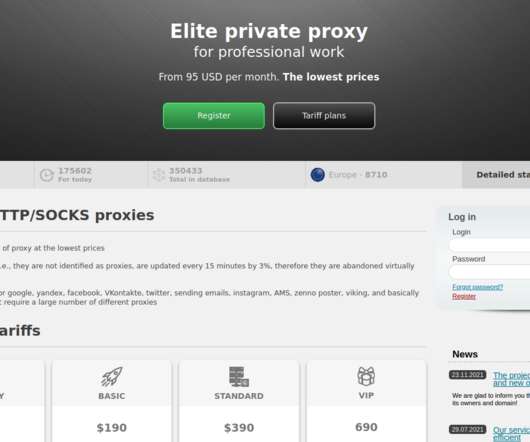
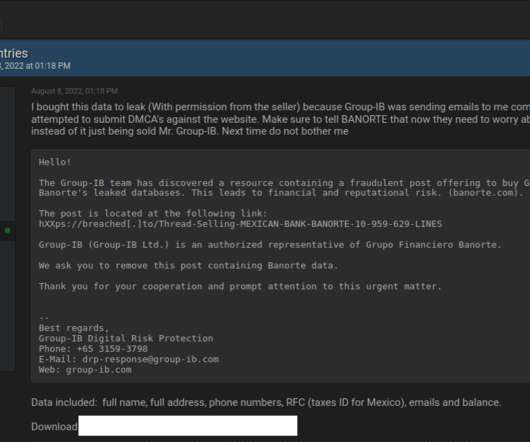
Google continues to struggle with cybercriminals running malicious ads on its search platform to trick people into downloading booby-trapped copies of popular free software applications. 252 do serve actual software downloads, but none of them are likely to be malicious if one visits the sites through direct navigation.

























Let's personalize your content