What Should CISOs Prioritize In A Volatile Landscape?: A Webinar With Top CyberSecurity Columnist Joseph Steinberg
Joseph Steinberg
OCTOBER 27, 2022
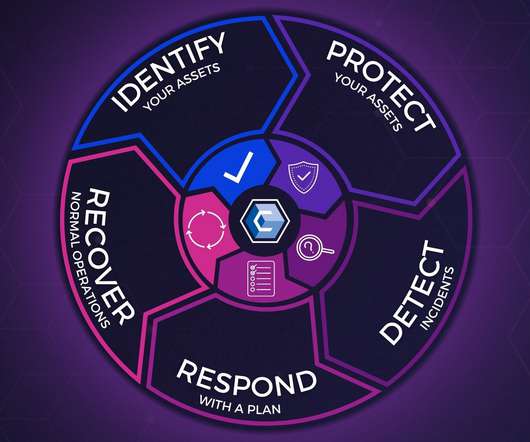
Have you been prioritizing Detection and Response over Protection when it comes to your cybersecurity strategy? All three, of course, are key pillars of the NIST cybersecurity framework – so, why are you prioritizing two of them over the third? In fact, in most cases, “Protect” should be the top priority. Join us for an insightful discussion with Joseph Steinberg and Venky Raju, as they discuss all manner of things related to proactive cybersecurity and Zero Trust.





































Let's personalize your content