Using Hacked LastPass Keys to Steal Cryptocurrency
Schneier on Security
SEPTEMBER 18, 2023
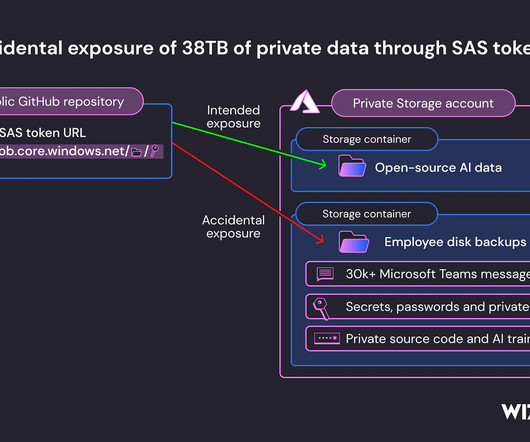
Remember last November, when hackers broke into the network for LastPass—a password database—and stole password vaults with both encrypted and plaintext data for over 25 million users? Well, they’re now using that data break into crypto wallets and drain them: $35 million and counting, all going into a single wallet. That’s a really profitable hack.







































Let's personalize your content