Many Public Salesforce Sites are Leaking Private Data
Krebs on Security
APRIL 27, 2023
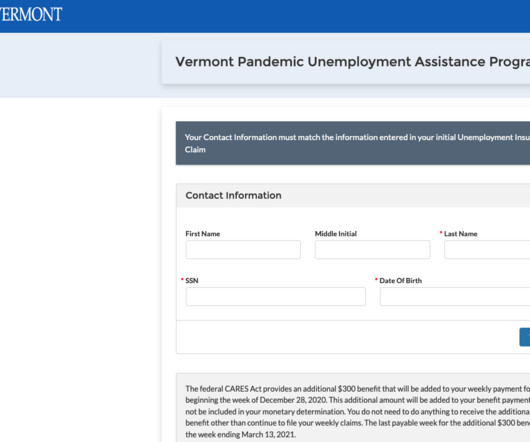
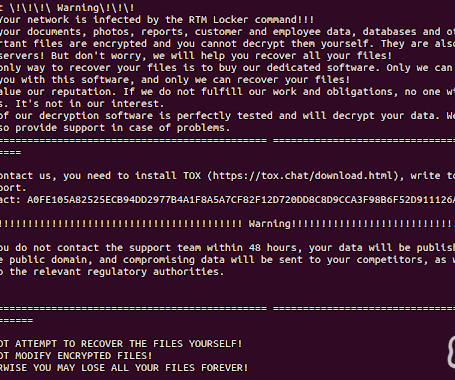
A shocking number of organizations — including banks and healthcare providers — are leaking private and sensitive information from their public Salesforce Community websites, KrebsOnSecurity has learned. The data exposures all stem from a misconfiguration in Salesforce Community that allows an unauthenticated user to access records that should only be available after logging in.









































Let's personalize your content