Pro-Russia hackers NoName057 targets Italy again after Zelensky’s visit to the country
Security Affairs
JANUARY 12, 2025
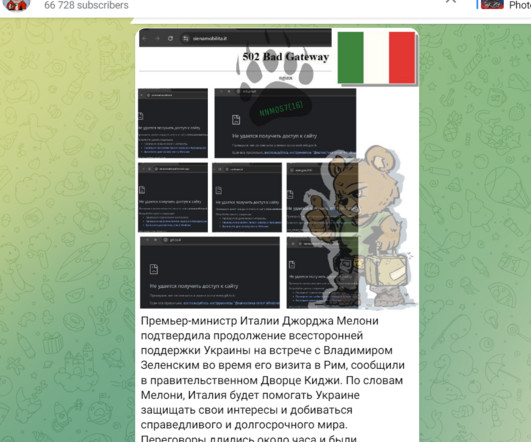
Over the weekend, Italy faced new waves of DDoS attacks carried out by pro-Russia group NoName057(16). Pro-Russia hackers Noname057(16) targeted Italian ministries, institutions, critical infrastructure’s websites and private organizations over the weekend. The new wave of attacks coincides with the visit of Ukrainian President Volodymyr Zelensky to Italy.



















Let's personalize your content