Fake AI Video Tools Spreading New “Noodlophile” Malware, Targets Thousands on Facebook
eSecurity Planet
MAY 11, 2025
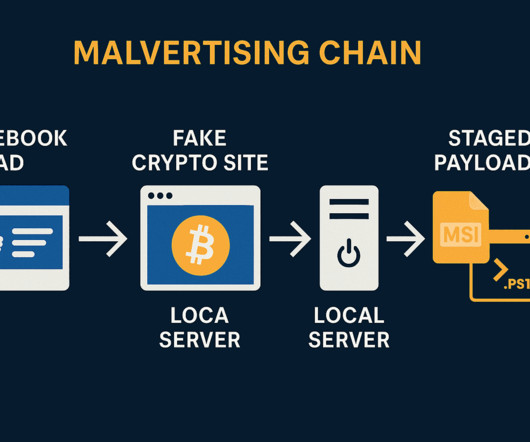
IT executive updating AI systems using green screen laptop, writing intricate binary code scripts. Technical support consultant using programming to upgrade artificial intelligence simulation model As AI tools boom in popularity, cyberthieves are exploiting the excitement with fake AI video editing platforms that lure users into downloading malware.






































Let's personalize your content