Apple’s Device Analytics Can Identify iCloud Users
Schneier on Security
NOVEMBER 22, 2022
Troy Hunt
NOVEMBER 22, 2022
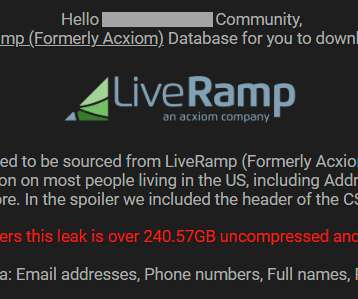
If you find your name and home address posted online, how do you know where it came from? Let's assume there's no further context given, it's just your legitimate personal data and it also includes your phone number, email address. and over 400 other fields of data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
NOVEMBER 22, 2022
Endpoints are where all are the connectivity action is. Related: Ransomware bombardments. And securing endpoints has once more become mission critical. This was the focal point of presentations at Tanium’s Converge 2022 conference which I had the privilege to attend last week at the Fairmont Austin in the Texas capital. I had the chance to visit with Peter Constantine, Tanium’s Senior Vice President Product Management.
Security Affairs
NOVEMBER 22, 2022
Let’s give a look at API vulnerabilities by reading the API Security Top 10 published by the Open Web Application Security Project (OWASP).
Speaker: William Hord, Vice President of ERM Services
Join us as we discuss the various tangents of data and the change management process that will help you make better risk-based business decisions to save time and money for your organization.
Dark Reading
NOVEMBER 22, 2022
Google Workspace's team is seeing a spike in phishing and spam hitting Gmail — up 10% in just the last two weeks
Naked Security
NOVEMBER 22, 2022
Review your servers, your patches and your authentication policies - there's a proof-of-concept out. Microsoft Uncategorized Vulnerability 0 day :ProxyNotShell CVE-2022-41040 CVE-2022-41082 Zero Day
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
CyberSecurity Insiders
NOVEMBER 22, 2022
Daixin, the Ransomware spreading group that hacked into the servers of AirAsia now seems to repent for its deeds, as it released a press statement that confirms that the victimized firm’s IT infrastructure, staff, and security are so poorly aligned that the said group of cyber criminals do not want to strike the same victim twice.
Dark Reading
NOVEMBER 22, 2022
Orgs are in the middle of a rapid increase in the use of new collaboration tools to serve the needs of an increasingly dispersed workforce — and they're paying a very real security price
Security Affairs
NOVEMBER 22, 2022
A researcher revealed how to bypass some of the filters in Cisco Secure Email Gateway appliance and deliver malware using specially crafted emails.
CyberSecurity Insiders
NOVEMBER 22, 2022
Killnet, the hacking group that works for Russian interests, is targeting UK’s Royal Family websites from the past few days. The attacks are of ‘Distributed Denial of Service (DDoS)’ variant and supposedly seem to take revenge digitally.

Speaker: Ronald Eddings, Cybersecurity Expert and Podcaster
In this webinar, Ronald Eddings, Cybersecurity Expert, will outline the relationship between SaaS apps and IT & security teams, along with several actionable solutions to overcome the new difficulties facing your organization.
Dark Reading
NOVEMBER 22, 2022
Cybercrooks have drained DraftKings accounts of $300K in the past few days thanks to credential stuffing, just as the 2022 FIFA World Cup starts up
Security Affairs
NOVEMBER 22, 2022
The Emotet malware is back and experts warn of a high-volume malspam campaign delivering payloads like IcedID and Bumblebee.
CyberSecurity Insiders
NOVEMBER 22, 2022
Stories from the SOC is a blog series that describes recent real-world security incident investigations conducted and reported by the AT&T SOC analyst team for AT&T Managed Extended Detection and Response customers. Executive summary. Humans are considered the weakest link in cybersecurity.
Security Boulevard
NOVEMBER 22, 2022
For many organizations, the complexity of security and compliance is still beyond their reach. Also, striking a balance between security and people, process and technology versus the risk/reward was something that both security leaders and business leaders need to confront and deal with every day.

Speaker: Karl Camilleri, Cloud Services Product Manager at phoenixNAP
Through a detailed analysis of major attacks and their consequences, Karl Camilleri, Cloud Services Product Manager at phoenixNAP, will discuss the state of ransomware and future predictions, as well as provide best practices for attack prevention and recovery.
Dark Reading
NOVEMBER 22, 2022
The Vietnam-based financial cybercrime operation's primary goal is to push out fraudulent ads via compromised business accounts

Security Boulevard
NOVEMBER 22, 2022
Spring Labs TrueZero enables companies to exchange sensitive data without revealing PII. Spring Labs launched TrueZero, a tokenization service that enables companies to exchange information with other financial institutions without ever revealing the underlying sensitive data.
CyberSecurity Insiders
NOVEMBER 22, 2022
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Phishing attacks are becoming more and more common, and they're only getting more sophisticated.
Security Boulevard
NOVEMBER 22, 2022
Zscaler ThreatLabz is always on the lookout for threat actors trying to take advantage of major world news and events.

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization. They’ll share how to grow your business faster and minimize costs for both security and compliance
CyberSecurity Insiders
NOVEMBER 22, 2022
UK Populace has reportedly lost £1000 last year on an average and the figure is said to double up this year, as Christmas shopping period has arrived a week before.
WIRED Threat Level
NOVEMBER 22, 2022
Finding high-quality detection canines is hard enough—and the pandemic only dug a deeper hole. Security Security / National Security
Dark Reading
NOVEMBER 22, 2022
To get the full picture, companies need to look into the cybersecurity history and practices of the business they're acquiring
Cisco CSR
NOVEMBER 22, 2022
Throughout my career, I have noticed the way we “futurize” technology. Often, we are thinking of technology in five-to-ten-year increments. But the fact of the matter is – technology is moving faster than we can keep up. The minute we think we understand it, it’s already onto something new.

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. Join Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies, for a discussion that will focus on compliance and the types of privacy and security measures your company should be aware of, as well as tips and methods for implementing these measures.
WIRED Threat Level
NOVEMBER 22, 2022
After months of meticulous planning, investigators finally move in to catch AlphaBay’s mastermind red-handed. Then the case takes a tragic turn. Backchannel Security Security / Cyberattacks and Hacks

Dark Reading
NOVEMBER 22, 2022
An AI's "world" only includes the data on which it was trained, so it otherwise lacks context — opening the door for creative attacks from cyber adversaries
Graham Cluley
NOVEMBER 22, 2022
The Daixin ransomware gang has given a humiliating slap in the face to Air Asia, which lost the personal data of five million passengers and all of its employees earlier this month. Data loss Malware Ransomware airline ransomware
Security Affairs
NOVEMBER 22, 2022
Researchers warn of threat actors employing a new Go-based malware dubbed Aurora Stealer in attacks in the wild. Aurora Stealer is an info-stealing malware that was first advertised on Russian-speaking underground forums in April 2022.
Dark Reading
NOVEMBER 22, 2022
As SASE adoption grows, with its allure of simplified protection via one network and security experience for hybrid workers, remember: Have an overall plan, integrate and migrate to scale usage, and start small
Cisco CSR
NOVEMBER 22, 2022
When you think about the most resilient creatures in the animal kingdom, what comes to mind? Perhaps the camel, which can survive for 6 months with no food or water. Or maybe it’s the honey badger, which tends to drink snake venom like cranberry juice. Or how about the immortal jellyfish?
Security Affairs
NOVEMBER 22, 2022
Two Estonian citizens were arrested in Tallinn for allegedly running a $575 million cryptocurrency fraud scheme. Two Estonian nationals were arrested in Tallinn, Estonia, after being indicted in the US for running a fraudulent cryptocurrency Ponzi scheme that caused more than $575 million in losses.
SecureWorld News
NOVEMBER 22, 2022
While a lot of the world's collective eyes are on the pitch in Qatar for the FIFA World Cup 2022, cybersecurity professionals are keeping their eyes on an uptick in cyberattacks against organizations in Arab countries.
Bleeping Computer
NOVEMBER 22, 2022
Microsoft said today that security vulnerabilities found to impact a web server discontinued since 2005 have been used to target and compromise organizations in the energy sector. [.]. Security Microsoft
Dark Reading
NOVEMBER 22, 2022
Cybercrime continues to evolve — and shows no signs of slowing down
Let's personalize your content