GUEST ESSAY: Advanced tools, tactics required to defend latest attack variant — ‘DeepSea phishing’
The Last Watchdog
JULY 14, 2022
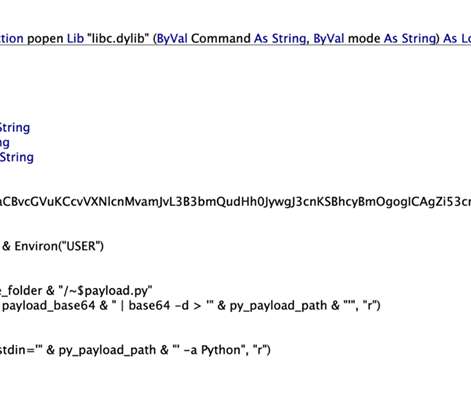
Phishing itself is not a new or a particularly complicated threat. But the emergence of advanced phishing techniques – “DeepSea Phishing” – poses an entirely new challenge for enterprises. Related: Deploying human sensors. Phishing comes with a simple premise – lure someone to interact with a malicious link, file, or credentials-input, disguised as a legitimate email or website.











































Let's personalize your content