NATO Adds Cyber Commitments, Potential Ransomware Response
Lohrman on Security
JUNE 20, 2021
The North Atlantic Treaty Organization (NATO) opened the door for cyber attacks to trigger “Article 5” actions. This is a big deal — here’s why.

Lohrman on Security
JUNE 20, 2021
The North Atlantic Treaty Organization (NATO) opened the door for cyber attacks to trigger “Article 5” actions. This is a big deal — here’s why.

Bleeping Computer
JUNE 20, 2021
With Microsoft getting ready to unveil the new Windows 11 operating system, we take a look at some of the new Registry hacks that can be used to customize your device. [.].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JUNE 20, 2021
A new bug in iPhone can permanently break users’ WiFi by disabling it, the issue could be triggered by simply connecting to a rogue hotspot. The researcher Carl Schou discovered a new bug in iPhone that can permanently break users’ WiFi by disabling it, the issue could be triggered by simply connecting to a rogue hotspot. . Once an iPhone established a WiFi connection to a rogue hotspot, it will no more be able to establish a connection to a Wi-Fi device, even if it is rebooted or th

Bleeping Computer
JUNE 20, 2021
A Georgia-based fertility clinic has disclosed a data breach after files containing sensitive patient information were stolen during a ransomware attack. [.].

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Affairs
JUNE 20, 2021
Norway police secret service states said that China-linked APT31 group was behind the 2018 cyberattack on the government’s IT network. Norway’s Police Security Service (PST) said that the China-linked APT31 cyberespionage group was behind the attack that breached the government’s IT network in 2018. The attribution of the attack to the APT31 grouo is based on the results of the investigation conducted by the Norwegian intelligence.
Bleeping Computer
JUNE 20, 2021
Windows 11 preview build recently leaked online, confirming the speculation and reports that the next generation of Windows is called "Windows 11". Thanks to the leaked build, we know pretty much everything about Windows 11. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Affairs
JUNE 20, 2021
Jaroslaw Kaczynski, the leader of the Poland Law and Justice party, blames Russia for the recent cyberattack targeting top Polish politicians. Jaroslaw Kaczynski, the leader of the Poland Law and Justice party (PiS), blames Russia for the recent cyberattack that targeted top Polish politicians. Last week, Poland’s parliament had a closed-door session to discuss an unprecedented wave of cyberattacks that hit its institutions and individuals.

Security Boulevard
JUNE 20, 2021
Our thanks to BSides Tampa for publishing their outstanding videos on the organization's YouTube channel. Enjoy the Education! Permalink. The post BSides Tampa 2021 – Rohini Sulatycki’s ‘Guardrails In The Cloud’ appeared first on Security Boulevard.

Security Affairs
JUNE 20, 2021
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the international press subscribe here. APWG: Phishing maintained near-record levels in the first quarter of 2021 BackdoorDiplomacy APT targets diplomats from Africa and the Middle East Security Affairs newsletter Round 318 Apple fixed 2 WebKit flaws exploited to target older iPhones G7 calls on Russia to d

Security Boulevard
JUNE 20, 2021
Our thanks to BSides Tampa for publishing their outstanding videos on the organization's YouTube channel. Enjoy the Education! Permalink. The post BSides Tampa 2021 – Jeremy Rasmussen’s ‘Ransomware – The Real Pandemic’ appeared first on Security Boulevard.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.
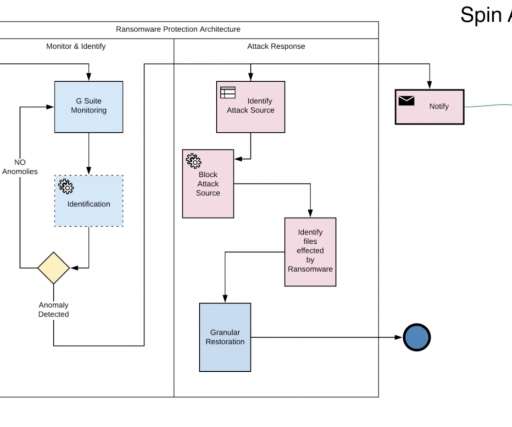
Spinone
JUNE 20, 2021
The purpose of this article is to outline the best practices for Office 365 security monitoring. This means it mainly focuses on detecting cyber threats. It also provides clear guidelines for Admins on how to supervise the cloud environment. For threat prevention and response, read our guide on Office 365 security best practices. Office 365 […] The post 6 Best Practices for Office 365 Security Monitoring for Administrators first appeared on SpinOne.

Security Boulevard
JUNE 20, 2021
Permalink. The post XKCD ‘Alien Visitors’ appeared first on Security Boulevard.
Let's personalize your content