Looking Back at the Colonial Pipeline Ransomware Incident
Lohrman on Security
MAY 8, 2022
In early May 2021, the world was shocked into attention by a ransomware attack that brought down gas lines. What have we learned — or not — one year later?
Lohrman on Security
MAY 8, 2022
In early May 2021, the world was shocked into attention by a ransomware attack that brought down gas lines. What have we learned — or not — one year later?

Security Boulevard
MAY 8, 2022
In the world of cybersecurity, various types of penetration testing exist, but before we explore the various kinds, what is penetration testing? A penetration test intends to identify network, system, or application vulnerabilities of an organization. These loopholes are then shared with decision-makers, who choose whether or not to rectify them. A penetration tester submits […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
MAY 8, 2022
Security researchers are warning F5 BIG-IP admins to immediately install the latest security updates after creating exploits for a recently disclosed critical CVE-2022-1388 remote code execution vulnerability. [.].

Security Boulevard
MAY 8, 2022
In early May 2021, the world was shocked into attention by a ransomware attack that brought down gas lines. What have we learned — or not — one year later? The post Looking Back at the Colonial Pipeline Ransomware Incident appeared first on Security Boulevard.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Malwarebytes
MAY 8, 2022
While we recently “ celebrated ” World Password Day, almost every security outlet keeps telling us that passwords alone are not enough. In practice, in the last few years this has meant pairing passwords with something else, such as a one-time code from an app or an SMS message, in a scheme called two-factor authentication ( 2FA ). But while pairing passwords with a second factor is much better than using a password by itself, it is just a way of working around some very serious, inh

Bleeping Computer
MAY 8, 2022
The RubyGems package repository has fixed a critical vulnerability that would allow anyone to unpublish ("yank") certain Ruby packages from the repository and republish their tainted or malicious versions with the same file names and version numbers. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
MAY 8, 2022
Google is now blocking Russian users and developers from downloading or updating paid applications from the Google Play Store due to sanctions, starting Thursday. [.].

The Hacker News
MAY 8, 2022
The U.S. State Department has announced rewards of up to $10 million for any information leading to the identification of key individuals who are part of the infamous Conti cybercrime gang. Additionally, it's offering another $5 million for intelligence information that could help arrest or convict individuals who are conspiring or attempting to affiliate with the group in a ransomware attack.

Bleeping Computer
MAY 8, 2022
A credit card stealing service is growing in popularity, allowing any low-skilled threat actors an easy and automated way to get started in the world of financial fraud. [.].

Security Affairs
MAY 8, 2022
This post provides a timeline of the events related to Russia invasion of Ukraine from the cyber security perspective. Below is the timeline of the events related to the ongoing Russia invasion that occurred in the previous weeks: May 06 – Anonymous and Ukraine IT Army continue to target Russian entities. The Anonymous collective and the volunteer group Ukraine IT Army continues to launch cyber attacks on Russian entities.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
MAY 8, 2022
Bridgecrew by Prisma Cloud is the codified cloud security platform built to bridge the gap between DevOps and security teams. Powered by automation, Bridgecrew empowers teams to find, fix, and prevent vulnerabilities, misconfigurations, and license compliance issues in source code, containerized applications, and infrastructure as code. With Bridgecrew’s platform, teams can streamline cloud security, enforce.
Security Affairs
MAY 8, 2022
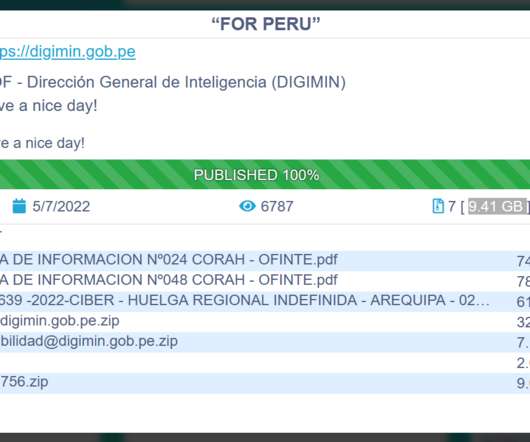
Conti Ransomware gang claims to have hacked the Peru MOF – Dirección General de Inteligencia (DIGIMIN) and stolen 9.41 GB. The Conti ransomware gang added the Peru MOF – Dirección General de Inteligencia (DIGIMIN) to the list of its victims on its Tor leak site. The National Directorate of Intelligence is the premier intelligence agency in Peru.

Security Boulevard
MAY 8, 2022
Josh Feinblum is the co-founder of Stavvy, a Boston-based fully integrated digital mortgage platform, where he leads product, engineering, people, and finance. He also serves as a venture partner at F-Prime Capital, where he evaluates and advises startups of all stages across multiple verticals. Josh talks to us about his journey through cybersecurity including his […].

Security Affairs
MAY 8, 2022
The American agricultural machinery manufacturer AGCO announced that has suffered a ransomware attack that impacted its production facilities. AGCO, one of the most important agricultural machinery manufacturers, announced that a ransomware attack impacted some of its production facilities. The company was forced to shut down portions of its IT systems in response to the incident.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
MAY 8, 2022
Most people preferred to download a virtual image of Kali Linux. The virtual machine is the best option to use multiple operating systems at a time. Kali Linux is the best operating system mostly used by hackers and penetration testers. On the official Kali Linux website, Virtual images are available for VMware and Virtual Box. […]. The post How to Download Virtual Image of Kali Linux appeared first on Security Boulevard.

Security Affairs
MAY 8, 2022
A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. Raspberry Robin spreads via removable USB devices Malware campaign hides a shellcode into Windows event logs US gov sanctions cryptocurrency mixer Blender also used by North Korea-linked Lazarus APT How the thriving fraud industry within Facebook a

Security Boulevard
MAY 8, 2022
Visit SecZetta in Person at Booth #7 and attend two speaking sessions 10-13, May, 2022, | Berlin Congress Center| Berlin, Germany & Online Fall River, Mass. May 6, 2022. The post SecZetta Brings Third-Party Identity Risk Solution to KuppingerCole European Identity Conference 2022 appeared first on SecZetta. The post SecZetta Brings Third-Party Identity Risk Solution to KuppingerCole European Identity Conference 2022 appeared first on Security Boulevard.

Security Affairs
MAY 8, 2022
The National Institute of Standards and Technology (NIST) has released updated guidance for defending against supply-chain attacks. The National Institute of Standards and Technology (NIST) has released updated guidance for defending against supply chain attacks. NIST has published the “ Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations ” in response to the Executive Order 14028: Improving the Nation’s Cybersecurity. “The purpose of this p

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
MAY 8, 2022
Visit SecZetta in Person at Booth #803 12-13 May| InterContinental London – The O2| London, England Fall River, Mass. (May 06, 2022) – Join SecZetta at the Gartner Identity. The post SecZetta Brings Third-Party Identity Solution to Gartner Identity & Access Management Summit 2022 appeared first on SecZetta. The post SecZetta Brings Third-Party Identity Solution to Gartner Identity & Access Management Summit 2022 appeared first on Security Boulevard.

Security Affairs
MAY 8, 2022
The US Government offers up to $15 million for information that helps identify and locate leadership and co-conspirators of the Conti ransomware gang. The US Department of State offers up to $15 million for information that helps identify and locate leadership and co-conspirators of the Conti ransomware gang. The reward is offered under the Department of State’s Transnational Organized Crime Rewards Program (TOCRP).

Security Boulevard
MAY 8, 2022
Global AppSec US 2021 Virtual Conference] 2 for publishing their well-crafted application security videos on the organization’s’ YouTube ** channel. Permalink. The post OWASP® Global AppSec US 2021 Virtual – Karthik Krishnamo’s ‘Application Security Playbook For Business’ appeared first on Security Boulevard.

The Security Ledger
MAY 8, 2022
A cyber attack has disrupted the operations of AGCO/Fendt, a major manufacturer of agricultural equipment, the company has acknowledged. The post Cyber Attack Halts Production at Ag Equipment Maker AGCO Fendt appeared first on The Security Ledger with Paul F. Roberts. Related Stories Feel Good Ukraine Tractor Story Highlights Ag Cyber Risk DEF CON: Security Holes in Deere, Case IH Shine Spotlight on Agriculture Cyber Risk Episode 218: Denial of Sustenance Attacks -The Cyber Risk To Agriculture.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.
Security Boulevard
MAY 8, 2022
via the comic artistry and dry wit of Randall Munroe , resident at XKCD ! Permalink. The post XKCD ‘Deep End’ appeared first on Security Boulevard.

Security Boulevard
MAY 8, 2022
Our thanks to both the OWASP® Foundation and the OWASP Global AppSec US 2021 Virtual Conference for publishing their well-crafted application security videos on the organization’s’ YouTube channel. Permalink. The post OWASP® Global AppSec US 2021 Virtual – Kim Carter’s ‘Purple Teaming With OWASP® PurpleTeam’ appeared first on Security Boulevard.
Let's personalize your content