QR Code Scam
Schneier on Security
DECEMBER 28, 2022
An enterprising individual made fake parking tickets with a QR code for easy payment.

Schneier on Security
DECEMBER 28, 2022
An enterprising individual made fake parking tickets with a QR code for easy payment.
Tech Republic Security
DECEMBER 28, 2022
A password manager can keep your sensitive information in-house. Here's how to deploy Passbolt to your data center or cloud-hosted service. The post How to deploy a self-hosted instance of the Passbolt password manager appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
DECEMBER 28, 2022
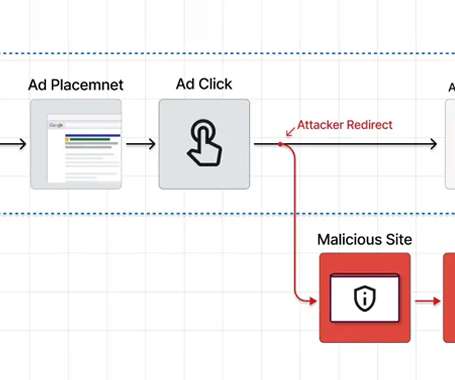
Malware operators have been increasingly abusing the Google Ads platform to spread malware to unsuspecting users searching for popular software products. [.].

CyberSecurity Insiders
DECEMBER 28, 2022
Smart Phones have become a need for us these days as they assist us in commuting, help in entertaining us if/when bored, help communicate with near & dear, read news and do more such stuff. But as these gadgets have turned crucial in our lives, many hackers are also interested in infiltrating them, to get our glimpse of our lives or where we are heading. .

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
WIRED Threat Level
DECEMBER 28, 2022
The password manager's most recent data breach is so concerning, users need to take immediate steps to protect themselves.
Security Boulevard
DECEMBER 28, 2022
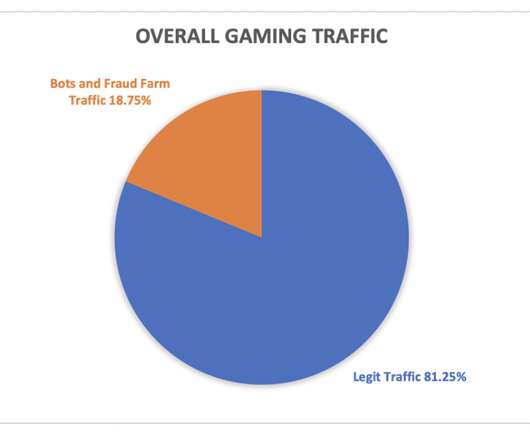
As the holiday season ramps up, online gamers spend more time in their favorite virtual worlds. From Nintendo to Xbox to “God of War” and “Call of Duty,” a flood of video games appear on the scene, encouraging players to invest even more time and money in this form of competitive entertainment. There are an […]. The post Gaming Companies Take Big Risks This Holiday appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
DECEMBER 28, 2022
The world is full of machines and gadgets, readily participating in the race to automation, though, this race incorporates a hoard of convolutions. Albeit, IoT is the escape route to push these convolutions at bay, so IoT security plays a prime role. The interconnecting machines’ network that supports effortless data exchange is popularly termed IoT […].

CSO Magazine
DECEMBER 28, 2022
The Log4Shell critical vulnerability that impacted millions of enterprise applications remains a common cause for security breaches a year after it received patches and widespread attention and is expected to remain a popular target for some time to come. Its long-lasting impact highlights the major risks posed by flaws in transitive software dependencies and the need for enterprises to urgently adopt software composition analysis and secure supply chain management practices Log4Shell , official
Security Boulevard
DECEMBER 28, 2022
4 Reasons Why Security and Compliance Are Critical for Operational Resilience . Managing cybersecurity and compliance is always challenging, but it was even more so post-pandemic. As threat actors took advantage of changing business environments such as more remote teams and rapid technology adoption, cyber and compliance moved front and center. .

Bleeping Computer
DECEMBER 28, 2022
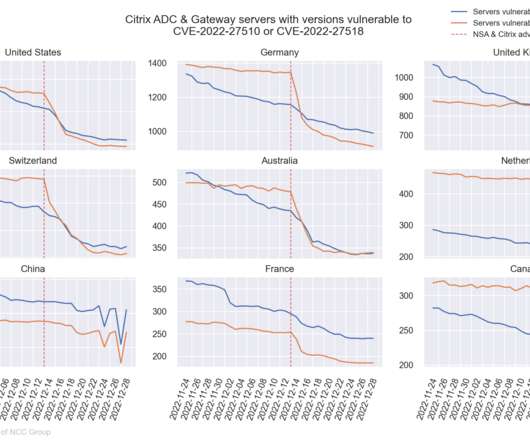
Thousands of Citrix ADC and Gateway deployments remain vulnerable to two critical-severity security issues that the vendor fixed in recent months. [.].

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

The Hacker News
DECEMBER 28, 2022
Decentralized multi-chain crypto wallet BitKeep on Wednesday confirmed a cyberattack that allowed threat actors to distribute fraudulent versions of its Android app with the goal of stealing users' digital currencies.
Dark Reading
DECEMBER 28, 2022
According to the FBI and Internet Crime Complaint Center, 25% of ransomware complaints involve healthcare providers.

CyberSecurity Insiders
DECEMBER 28, 2022
Most of you connected to the world of data are in a misconception that both the terms data privacy and data security are same and are just the synonyms. But that’s not correct and here’s an explanation: Data Privacy is the word used to the practice of handling the data like how it is being collected, stored, used and whether it is covered under any compliance.

Dark Reading
DECEMBER 28, 2022
This is what happens when a CISO gets tired of reacting to attacks and goes on the offensive.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

CyberSecurity Insiders
DECEMBER 28, 2022
For the first time, the hackers group that is being sponsored by North Korea State government is found spreading ransomware on computer networks related to companies and organizations operating in South Korea. According to the intelligence gathered by the National Police Agency of South Korea, the Kim Jong UN funded hacking groups were caught stealing email and identity related credentials related to over 890 foreign policy proficients in the past few weeks.
The Hacker News
DECEMBER 28, 2022
Users searching for popular software are being targeted by a new malvertising campaign that abuses Google Ads to serve trojanized variants that deploy malware, such as Raccoon Stealer and Vidar.

Dark Reading
DECEMBER 28, 2022
Will the bottom falling out of the cryptocurrency market have a profound impact on cybercriminal tactics and business models? Experts weigh in on what to expect.

Heimadal Security
DECEMBER 28, 2022
The world’s largest cryptocurrency mining pool, BTC.com, announced it was the victim of a cyberattack that resulted in the theft of approximately $3 million worth of crypto assets. BTC.com is the seventh largest cryptocurrency mining pool, accounting for 2.66% of the network’s total hash rate, according to its mining pool tracker. Some Stolen Assets Recovered […].

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Security Boulevard
DECEMBER 28, 2022
Here are 4 cybersecurity trends for 2023 as IT teams and stakeholders turn their attention to implementing defensive strategies. The post Four Cybersecurity Predictions for 2023 appeared first on Enzoic. The post Four Cybersecurity Predictions for 2023 appeared first on Security Boulevard.

Javvad Malik
DECEMBER 28, 2022
It was bound to happen – welcome to the future! Mom took her daughter to see a show. AI facial recognition software recognizes her and she’s unceremoniously escorted out by security. . Her offence? Her employer, a huge law firm (not her) is in protracted litigation with the owner MSG Entertainment, and MSG has a policy that precludes attorneys pursuing active litigation against the company from attending events at their venues.

Security Boulevard
DECEMBER 28, 2022
2022 was the year of the rise of the SBOM. This time of year, we take a look back at the havoc wreaked by breaches–that occurred in 2021 and earlier. The fallout from SolarWinds and Kaseya cyberattacks continued into 2022, which poignantly illustrated how vulnerable the software supply chain is. The Log4j open-source vulnerability at. 2022 was the year of the SBOM…and 2023 will be, too .
Security Affairs
DECEMBER 28, 2022
The chief executive of insurance giant Zurich warns that cyber attacks, rather than natural catastrophes, will become uninsurable. Mario Greco, chief executive of insurer giant Zurich, has warned that cyber attacks will become soon “uninsurable.”. The attacks are becoming even more frequent and the damage they are causing continues to grow. “What will become uninsurable is going to be cyber,” Mario Greco told the Financial Times.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Heimadal Security
DECEMBER 28, 2022
The Federal Bureau of Investigation (FBI) issued an alert about cyber criminals using a new methodology to defraud users – brand impersonation via search engine advertisement services. The victims are led to malicious websites that host ransomware and steal login credentials and other financial information. At first, cyber criminals buy advertisements that appear in internet […].

Security Affairs
DECEMBER 28, 2022
Decentralized multi-chain crypto wallet BitKeep lost over $9 Million worth of digital currencies after a cyber attack. BitKeep was the victim of a supply chain attack that resulted in the theft of over $9 Million worth of digital currencies from its customers. The attack took place on December 26, threat actors were able to distribute tainted versions of the company’s Android app that were designed to steal users’ digital assets.

Naked Security
DECEMBER 28, 2022
If the crooks have connected up your phone number and your Twitter handle. what could go wrong?

Dark Reading
DECEMBER 28, 2022
It's time companies build a multilayered approach to cybersecurity.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Boulevard
DECEMBER 28, 2022
As the year is coming to an end, I can’t help but take a walk down memory lane to reminisce and reflect on the journey of the cloud threat landscape. Here’s my take on this 2022 recap of cloud threats. First things first, I think it’s safe to say that this year has been a rollercoaster of non-stop cyberattacks. Particularly the cloud threat landscape, it truly feels like the massive potholes in front of my home.
Fox IT
DECEMBER 28, 2022
Authored by Yun Zheng Hu. Recently, two critical vulnerabilities were reported in Citrix ADC and Citrix Gateway; where one of them was being exploited in the wild by a threat actor. Due to these vulnerabilities being exploitable remotely and given the situation of past Citrix vulnerabilities , RIFT started to research on how to identify the exact version of Citrix ADC and Gateway servers on the internet so that we could inform customers if they hadn’t patched yet.

Bleeping Computer
DECEMBER 28, 2022
The Royal Ransomware gang claimed responsibility for a cyber attack against telecommunications company Intrado on Tuesday. [.].

Security Boulevard
DECEMBER 28, 2022
Cloud Security Provider Names Ben McGucken to Head Federal Sales and Announces Support for AWS GovCloud (US) and Azure for US Government BOSTON & TEL AVIV, Israel, September 14, 2022–(BUSINESS WIRE)–Ermetic, the cloud infrastructure security company, today announced that it has initiated the process to achieve Authority to Operate (ATO) status under the Federal Risk […].

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content