De-anonymization Story
Schneier on Security
JULY 28, 2021
Tech Republic Security
JULY 28, 2021
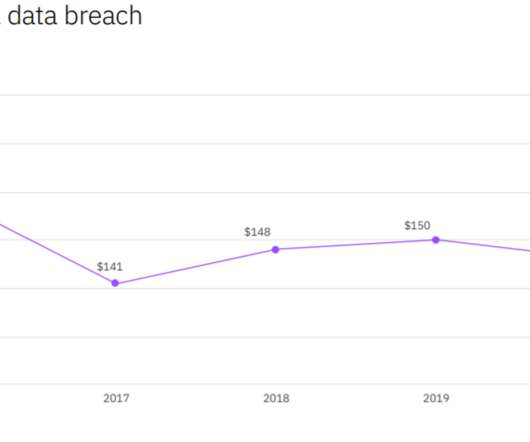
The average cost of a data breach among companies surveyed for IBM Security reached $4.24 million per incident, the highest in 17 years
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Hacker News
JULY 28, 2021
A Chinese cyberespionage group known for targeting Southeast Asia leveraged flaws in the Microsoft Exchange Server that came to light earlier this March to deploy a previously undocumented variant of a remote access trojan (RAT) on compromised systems.
Security Boulevard
JULY 28, 2021
Accelerate Open Banking Innovation with These 7 Data Capabilities. michelle. Wed, 07/28/2021 - 12:34. The inability to automate data impedes time to market with open APIs and banking features at over half of Europe’s banks, according to new research. Kobi Korsah. Jul 28, 2021.

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization. They’ll share how to grow your business faster and minimize costs for both security and compliance
Security Affairs
JULY 28, 2021
The ‘Cost of a Data Breach’ report commissioned by IBM Security states that the cost of a data breach exceeded $4.2 million during the COVID19 pandemic.
CSO Magazine
JULY 28, 2021
More applications and devices are using password repositories to check on password reuse. When you log into your iPhone for example, it now alerts you that passwords you saved in your iCloud keychain may have been reused in other places.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
CSO Magazine
JULY 28, 2021
What is D3FEND? D3FEND is a new schema released by Mitre last month to establish a common language to help cyber defenders share strategies and methods. It is a companion project to the company’s ATT&CK framework. While complementary, the two projects are very different.
CyberSecurity Insiders
JULY 28, 2021
According to a report from Sky News, a UK based Aerospace company was targeted by a phishing attack, where a top official from the company was befriended by an Iranian hacker in disguise of a beautiful Aerobics Instructor named Marcella Flores.
Tech Republic Security
JULY 28, 2021
The number of ads selling access to corporate networks has continued to increase from 2019 to 2020 and into 2021, says Positive Technologies
Security Affairs
JULY 28, 2021
BlackMatter ransomware gang, a new threat actor appears in the threat landscape and claims to combine TTPs of Darkside and REvil. BlackMatter is a new ransomware gang that started its activity this week, the cybercriminals group claims to be the successor of Darkside and REvil groups.

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. Join Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies, for a discussion that will focus on compliance and the types of privacy and security measures your company should be aware of, as well as tips and methods for implementing these measures.
eSecurity Planet
JULY 28, 2021
Whether perceived or real, a lack of understanding about blockchain technology has slowed the adoption of advanced distributed database technology in the past decade.
The Hacker News
JULY 28, 2021
An Iranian cyberespionage group masqueraded as an aerobics instructor on Facebook in an attempt to infect the machine of an employee of an aerospace defense contractor with malware as part of a years-long social engineering and targeted malware campaign.
CSO Magazine
JULY 28, 2021
Cloud workloads, deployed into highly dynamic environments, typically use and coexist with a wide range of cloud providers and third-party platforms and services.
Security Boulevard
JULY 28, 2021
How is Cloud Infrastructure Security Important for an Organization? Embracing new technologies lead to qualitative growth but simultaneously holds high chances of quantitative data breaches.

Dark Reading
JULY 28, 2021
Security researchers and practitioners share a host of new cyber tools for penetration testing, reverse engineering, malware defense, and more

Security Boulevard
JULY 28, 2021
We are in the digital age where our lives depend on the internet of things. A career in computer science attracts the highest starting points in salaries. Career opportunities are numerous and this gives the experts a wide range of choice for computer experts.
CyberSecurity Insiders
JULY 28, 2021
The Big Iron OS of IBM was upgraded a short while ago to address all issues related to provisioning and use of Linux applications and utilities.
Security Boulevard
JULY 28, 2021
The long gas lines, panic buying and price spikes are fading into memory. But the ransomware attack in early May 2021 on the largest fuel pipeline in the U.S. must continue to drive urgent action by the industry and policymakers to protect the nation’s key infrastructure.
eSecurity Planet
JULY 28, 2021
The FBI and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) joined counterparts in the UK and Australia today to announce the top 30 vulnerabilities exploited since the start of the pandemic.
Security Affairs
JULY 28, 2021
A China-linked cyberespionage group, tracked as PKPLUG, employed a previously undocumented strain of a RAT dubbed THOR in recent attacks.
Security Boulevard
JULY 28, 2021
Multi-factor authentication (MFA) is one step which everyone should be taking to add an extra layer of security to account logins. The post Why You Need to Get Serious About Multi-Factor Authentication appeared first on Security Boulevard. Security Bloggers Network
We Live Security
JULY 28, 2021
Twitter’s transparency report revealed that users aren’t quick to adopt 2FA and once they do enable it, they choose the least secure option. The post Most Twitter users haven’t enabled 2FA yet, report reveals appeared first on WeLiveSecurity
The Hacker News
JULY 28, 2021
An Android malware that was observed abusing accessibility services in the device to hijack user credentials from European banking applications has morphed into an entirely new botnet as part of a renewed campaign that began in May 2021.
We Live Security
JULY 28, 2021
With vacations in full swing, cybercriminals will be looking to scam vacationers looking for that perfect accommodation. The post Booking your next holiday? Watch out for these Airbnb scams appeared first on WeLiveSecurity. Cybersecurity

Naked Security
JULY 28, 2021
Ut tensio, sic uis! Does twice the bug pile on twice the pressure to fix it? Apple Microsoft Vulnerability disclosure Exploit vulnerability
Security Boulevard
JULY 28, 2021
Each month in 2021, NTT Application Security has been tracking the state of application security and the threat landscape, paying particular attention to the window of exposure (WoE), vulnerability by class and time to fix.
Bleeping Computer
JULY 28, 2021
Technical details are now available for a vulnerability that affects Hyper-V, Microsoft's native hypervisor for creating virtual machines on Windows systems and in Azure cloud computing environment. [.]. Security

Security Boulevard
JULY 28, 2021
With so much news about malware, organizations everywhere are working to protect their systems, networks, software, and devices from infection. However, many are still primarily relying on detection-based solutions that malware can easily evade.
Cisco Retail
JULY 28, 2021
It’s a Monday morning and you’re opening up your laptop to start another week of work. Your weekly team meeting pops up on your calendar and you sigh as you set down your cup of coffee to join the conference call. The usual chatter of “How was your weekend?”
Security Boulevard
JULY 28, 2021
Addressing security fatigue with small changes to your AppSec strategy can help you manage and minimize risks in your applications. . The post How to cyber security: Addressing security fatigue appeared first on Software Integrity Blog.
SecurityTrails
JULY 28, 2021
A while back, SecurityTrails announced that they would be running a contest dubbed "Recon Master". The aim of the game is to find hostnames that resolve to an IPv4 address that are not already found by SecurityTrails.
Malwarebytes
JULY 28, 2021
The 2020 Olympics are, after a bit of a delayed start , officially in full swing. So too is the possibility for scammers to crawl out of the woodwork.
Threatpost
JULY 28, 2021
They’re either new or old REvil & DarkSide wine in new bottles. Both have a taste for deep-pocketed targets and DarkSide-esque virtue-signaling. Malware News Web Security
Bleeping Computer
JULY 28, 2021
Northern Ireland's Department of Health (DoH) has temporarily halted its COVID-19 vaccine certification web service and mobile apps following a data exposure incident. [.]. Security
Heimadal Security
JULY 28, 2021
The LockBit ransomware was launched in September 2019 as a ransomware-as-a-service.
Let's personalize your content