Developer Sabotages Open-Source Software Package
Schneier on Security
MARCH 21, 2022
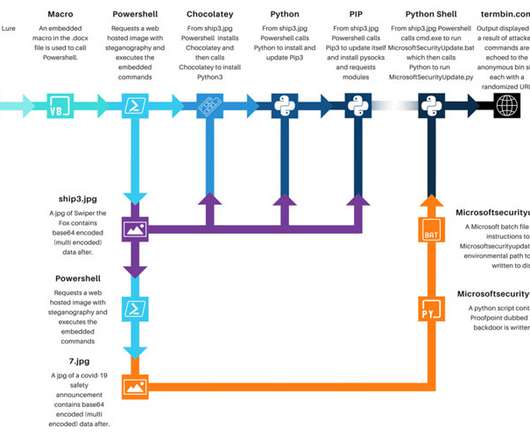
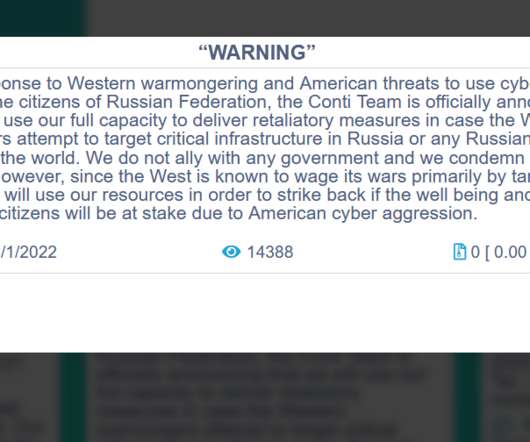
This is a big deal : A developer has been caught adding malicious code to a popular open-source package that wiped files on computers located in Russia and Belarus as part of a protest that has enraged many users and raised concerns about the safety of free and open source software. The application, node-ipc, adds remote interprocess communication and neural networking capabilities to other open source code libraries.









































Let's personalize your content