Feds Charge Five Men in ‘Scattered Spider’ Roundup
Krebs on Security
NOVEMBER 21, 2024
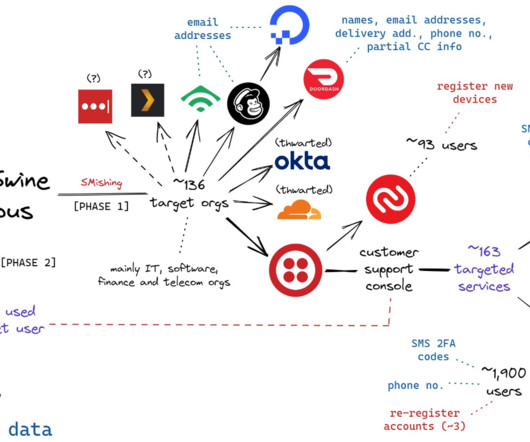
Federal prosecutors in Los Angeles this week unsealed criminal charges against five men alleged to be members of a hacking group responsible for dozens of cyber intrusions at major U.S. technology companies between 2021 and 2023, including LastPass , MailChimp , Okta , T-Mobile and Twilio. A visual depiction of the attacks by the SMS phishing group known as Scattered Spider, and Oktapus.









































Let's personalize your content