Accused ‘Raccoon’ Malware Developer Fled Ukraine After Russian Invasion
Krebs on Security
OCTOBER 31, 2022
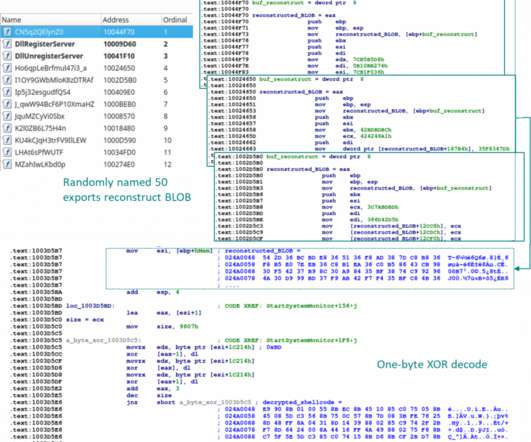
A 26-year-old Ukrainian man is awaiting extradition from The Netherlands to the United States on charges that he acted as a core developer for Raccoon , a popular “malware-as-a-service” offering that helped paying customers steal passwords and financial data from millions of cybercrime victims. KrebsOnSecurity has learned that the defendant was busted in March 2022, after fleeing mandatory military service in Ukraine in the weeks following the Russian invasion.






































Let's personalize your content