Fines as a Security System
Schneier on Security
FEBRUARY 20, 2023
Tile has an interesting security solution to make its tracking tags harder to use for stalking: The Anti-Theft Mode feature will make the devices invisible to Scan and Secure, the company’s in-app feature that lets you know if any nearby Tiles are following you. But to activate the new Anti-Theft Mode, the Tile owner will have to verify their real identity with a government-issued ID, submit a biometric scan that helps root out fake IDs, agree to let Tile share their information with law e
















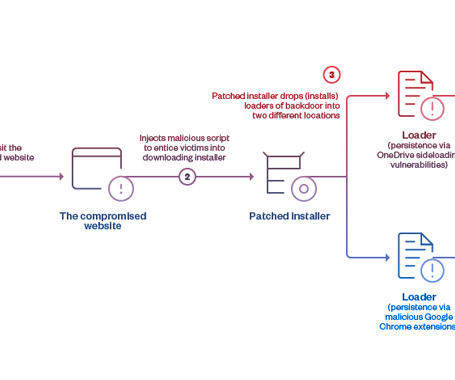

























Let's personalize your content